It’s hard for me to even think about Donald Trump, and his various craptastic election fraud maneuvers. But, when I do, my world rapidly turns into a throbbing sea of anger. Sure, I am most angry at Trump and his inane clown posse, but there’s enough to go around.
My anger gets so profound, sometimes, that I simply cannot bear to think about certain things, because I’ll just go around in a funk, muttering curses at the obviousness and stupidity of everything. I’ve had to stop listening entirely to some of my former favorite podcasts, because my anger and contempt at the stupidity of the media also leaves me breathlessly sitting in my chair, twitching my fingers at thin air as if typing on a nonexistent keyboard.
Some background may be necessary. I was, once, one of the world’s top computer security consultants. I’m not going to bother with false modesty. I solved interesting problems, sometimes under intense time pressure, for a variety of clients. It’s a safe bet that you’ve heard about at least two of the incident responses I was involved in, or used a product based on one of my designs from the 90s, or used a system I consulted on regarding how to improve its overall security. For example, TASER was one of my clients; I helped design and reviewed the design of a tamperproof back-haul system that would ensure cop-cam data got safely from the camera to a cloud server without any cop having a chance to see it, or alter it. Surprisingly many of my recommendations did not make the major police departments happy and I don’t know if they were implemented. I did data and security audits for Intuit, looking at their process whereby users were re-authenticated if they dropped offline for a while or change an email address and a residence address at the same time. A lot of those recommendations evolved into the many mechanisms you are doubtless familiar with, for re-establishing identity or changing a password. I taught system audit process for years, at a small company called Arthur Andersen, before losing that client to its own hubris. One of my most interesting cases involved the website of the US’ largest retailer, which went down at Christmas time – the IT department claimed it was a denial of service attack by hackers, but I did some creative (and if I may say, fascinating) data analysis on the log files, and demonstrated conclusively that the crashes were a result of peak system load causing an unexpected interaction that would have been caught and corrected had the IT department invested some time in system performance analysis. As a psych major, and a former UNIX system performance tuner at Digital 1985-1987, I was uniquely positioned for this problem thanks to several semesters of statistics and years of digging through kernel performance profiles. My report was read at a board of directors meeting, and everyone on the systems side of the IT department got let go, and I was contracted to interview their replacements. I also served as a non-testifying expert in a number of patent cases, in which I was responsible for digging out the meat of the situation (infringing, or not…?) and aligning it with a claim-chart, explaining it to lawyers, and teaching the lawyers how to explain it to a judge. This is not a minor feat, teaching a lawyer how to explain to a jury what a translation lookaside buffer is, and why it’s important – well, it’s a job. Anyhow, in retrospect, I suppose I was having the time of my life, though often it seemed painful and exacting because basically everything I did had to be perfect because if I recommended the wrong thing, and my client took my advice and it blew up on them, well, it would have ended my career. Someone like me would have written a memo to the CEO and board of directors recommending that I be blacklisted, and then I’d have been free of my career, able to pursue the life of a starving artist. I was a consultant from 1995 until 2018, and I don’t think you could find anyone who’d ever say I fucked up a project.
The reason all of that is relevant is because I learned a couple of things:
1) Question things relentlessly. You want to understand how all the stuff works, and why it works and for whom at all times.
2) Do your research. Asking someone to explain stuff to you is all well and good, but you don’t learn much that way. The way to learn is to have someone explain it to you, then read the design documents, then the code, and then go back and have them explain the gaps. When I was working a project, I lived in data centers – literally – during one incident response I slept for 3 days on a pile of closed-cell foam from workstation boxes, because I could not stop staring at the log data I was rummaging through. In the course of those sorts of projects, it seemed that obssessively digging into things always paid off in the end, so I did that. Besides, doing your research is absolutely crucial if/when someone tries to bullshit you, and you open your notebook and start quoting actual measurements from actual results that contradict their theory. And that is relevant to this posting.
3) There is no such thing as useless knowledge. There is only knowledge you have not used, yet. I don’t believe in an afterlife, naturally, but if I did, I’d have an eternity in hell to lecture people about 4.2BSD kernel internals and filesystem design.

How to hack a computer. self-portrait 2009
So, imagine my surprise when someone made a few comments over at Daily Kos about election machine interference, and I did something I have not done for ages: I thought about election system security. Well, I was a consultant for Diebold, one year, regarding automatic teller machines, while my old friend Avi Rubin was working for them on the voting machines, and smeared egg all over their faces. [The ATMs are pretty good, except for one major flaw, which was considered a design choice] [I still do not agree with that choice, 20 years later, because they are still paying for it] I’ve also stood by and poured tequila shots and coca-cola chasers while watching the hackers at DEFCON tear apart voting machines. That always frustrated me, because the flaws that were found were usually the result of poor design choices forced upon the manufacturer by customers with unrealistic requirements. I.e.: “we don’t want it on a network, but we want the data to move over a network” nyuk, nyuk, nyuk. Having any system connected to a network means a) it is much more useful b) it is much more vulnerable, and now we are arguing about how to mitigate risks that have been taken on in the system as a consequence of the design choice. What if the network is isolated, encrypted, firewalled, and uses a value-added network instead of the public internet? Good question! Now we are into the weeds of details. This is an example of system analysis – arguing details about VANs and VPNs and SSL is risk mitigation, the tactics of computer security, whereas security by design is the strategy of how to mitigate whole categories of risks by not running them in the first place.
Now, I’d actually already thought through how to do secure transactions over untrusted networks [I taught a class on how to do this, at USENIX, for 2 years in the 90s] and as the internet began seeing a welter of malware, I got involved in detecting, then breaking and spoofing, malware command and control. Building a stealthy command/control channel is a seriously difficult technical trick and mostly entails figuring out how to hide communications within other communications. But, once you know the communication is happening, it’s relatively easy to pick it out – after all, it’s got to be predictable because that’s how command/control works. I’d developed tools for detecting this sort of stuff and concluded that making it hard is easy, but making it undetectable may be impossible. [ranum, dilley]
That is why I immediately ignored Sidney Powell as a mere crank, because there was all this nonsensical talk about Hugo Chavez and Dominion and Italy and I basically ignored it all because nobody was talking about command and control. “Call me when you’ve got something.” Also, I ignored it all as crankery because nobody credible was even being asked to look at something something that might indicate something. If Powell had said, “Bruce Schneier and Avi Rubin are leading a team of consultants who are reverse-engineering the command/control of a mysterious undocumented process that is running on Dominion voting machines…” I would have, well, I’d have waited – because calling Bruce would just get me “you know I can’t discuss any of this.” The kind of analysis I’d expect to eventually get would be something akin to Kaspersky Labs’ excellent dissection of Equation Group”‘s malware.[kaspersky] Equation Group is the NSA’s Tailored Access Operations (TAO). [Yes, I taught at NSA, too] Anyhow, if someone was remote controlling voting machines, where was the evidence? There would be evidence. Even NSA gets caught. Besides, if Hugo Chavez had hired someone to put mojo backdoors in voting machines, they would have hired … who? Building cyberweapons is kind of a niche skill, like disassembling cyberweapons is. But the fingerprints of a cyberweapon are absolutely clear, once you know it is there and can find its command/control, and demonstrate its function. I would be prepared to believe that there was an NSA-built command/control stack in a voting machine – since Dominion machines use Commercial Off The Shelf (COTS) hardware, I assume that means there are Intel processors in there, therefore if the CPU was made after 2012 it has a backdoor in it – called “Intel Management Engine” (IME) [intel] – unmistakeable fingerprints, like I said – it’s on the silicon. [hardware backdoors in X86 silicon] None of that stuff is Venezuelan. If you’re a US taxpayer, you helped fund it, not Hugo Chavez.
As soon as the republicans started talking about the vote machines being rigged, I knew I was listening to crankery for the simple reason that not all voting machines are created equal. In fact, its down to the state, and then down to the jurisdiction. When I vote at my polling place (Morrisdale Grange) we’re pretty low-throughput and use a system that has a touch interface which spits out a printed card of your choices, which are logged electronically and the printed cards are saved in case there is an audit. Sure, there are some cities where there are networked voting machines that are managed locally, but in some districts it’s one machine, in another it’s another, and there’s paper trails on all of them – that’s how the recounts/audits are done. I also talked to some of the locals, including our postmistress at our zip code (who believed the election was fraudulent) and asked, “would you not notice if you started having lots of vote by mail registrations sent through here to people who are dead?” See what I mean about questions unasked? It’s an obvious, simple question that anyone who was asserting ballot stuffing would have to be able to answer because it’s a prerequisite for ballot stuffing. Nobody appears to fucking think about this stuff at all, which is why it angers me so much – the questions ought to practically ask themselves:
“Excuse me, Mr Giuliani, if there were votes being injected into the voting machines electronically, why did they not register as a large discrepancy when there was a bi-partisan manual recount? If I added 10,000 votes electronically, there would be 10,000 missing paper cards. And, the voter rolls would be audited and the 10,000 additional votes would stick out like a sore thumb. There are probably 3,000 voters in my district and it’d be a huge discrepancy if one year my district cast 3,000 votes and suddenly the next year cast 13,000”
This is why I am pissed off at the whole US, right now: the media also failed horribly by not asking those rather obvious questions.
“Do you have any packet captures of the command/control that this alleged backdoor was using? Can you give us a description of how it functioned? Who do you have looking at it?”
Again, Bruce Schneier exists. All of us in security know of Bruce. If you google “computer security expert” it is more likely to pop up Bruce than anyone else (including me!) – did all the journalists in the USA get so dim-witted that they never thought to call Bruce or Avi on background? Now, I’m tempted to pick up a phone, myself, “Hey Avi, did any journalists call you about the whole Chavez thing?” but, I just emailed instead. I’ll update in the comments if I have any feedback from Bruce or Avi, I am genuinely curious.
But those are complicated technical questions that one cannot expect a former prosecutor, or a high-paid lawyer to be able to answer, or to have done the slightest bit of thinking about before starting their press conference. Here’s a simpler one: Rudi Giuliani made some manifestly false statements about Ruby Freeman and Shay Moss, and nobody cross-checked him about the obvious stuff:
Rudy: Freeman and Moss were “passing around USB ports like they were vials of heroin or cocaine.”
No Journalist Ever: “Mr Giuliani, a USB port is a fixed interface screwed into the back or motherboard of a computer – one does not ‘pass around’ a USB port. Did you perhaps mean a USB thumb drive?”
That’s the sound of the trap being cocked. This is what it sounds like being triggered:
No Journalist Ever: “Because, the voting machines in use in that jurisdiction are Dominion’s product, and the system architecture of the Dominion machines is published [here] and the Dominion systems run either Linux or Android/Linux. Ruby Freeman and Shay Moss would have had to be expert hackers, and they would have had to be using some kind of a live hack, or rebooting the system after reconfiguring the BIOS boot sequence, which – according to Dominion – is controlled and boot-locked. Can you tell us anything about Ruby Freeman and Shay Moss’ status among the international elite of hackers?”
There are other things that the journalists, mighty truth-seeking homing missiles they, forgot to ask about – voting machines go through a pretty impressive certification process including extremely careful configuration management. Stuff like system reboots are all logged. So, by the way, are USB drive insertions. All operating systems worth their salt record that kind of stuff. Here’s a screenie I borrowed from [techrepublic]
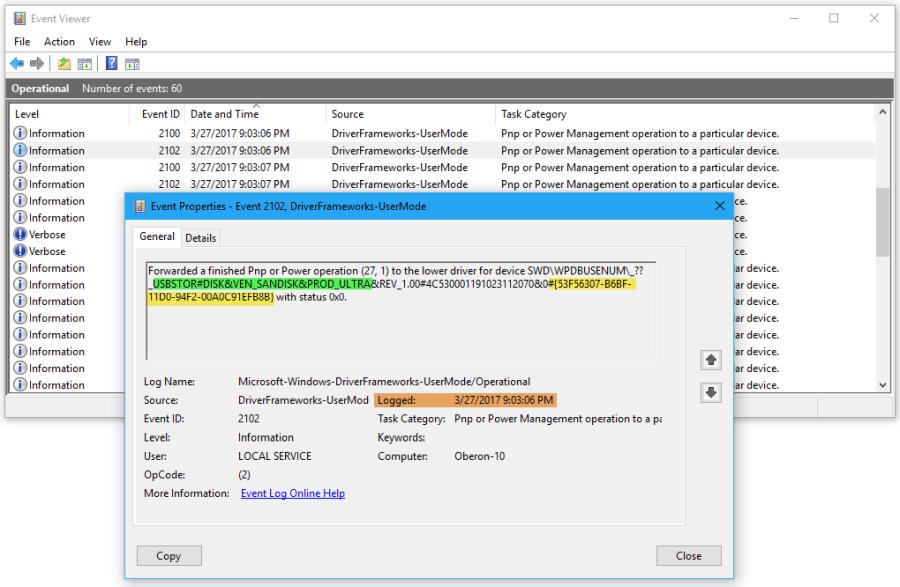
Even Windows manages to not fail at this truly basic stuff. Linux and BSD variants do it, too: [ubuntu]
May 25 07:31:25 tardis-w520 kernel: [ 161.469096] usb 1-1.5.5: new high-speed USB device number 8 using ehci_hcd
May 25 07:31:25 tardis-w520 mtp-probe: checking bus 1, device 8: "/sys/devices/pci0000:00/0000:00:1a.0/usb1/1-1/1-1.5/1-1.5.5"
May 25 07:31:25 tardis-w520 kernel: [ 161.658587] scsi6 : usb-storage 1-1.5.5:1.0
May 25 07:31:25 tardis-w520 kernel: [ 161.658685] usbcore: registered new interface driver usb-storage
May 25 07:31:25 tardis-w520 kernel: [ 161.795563] usbcore: registered new interface driver uas
“New high speed USB device” isn’t super clear, but you can also see it’s manifesting as as a SCSI pseudo-device, i.e.: a hard drive. Again, no journalist appears to have asked, “did anyone do a forensic analysis on those machines?”
I’m going to guess that no journalist appears to have asked that because journalists appear to generally be lazy, ignorant hacks who don’t do their basic research. A little more basic research would show that there’s a pretty well thought-out process for validating the integrity of election machines. Who’d’a thunk!? Sure, this is Canadian, but the US has similar processes (we tend not to put such details on the web, since it could become a roadmap for attempting to compromise the system or process) [ca]
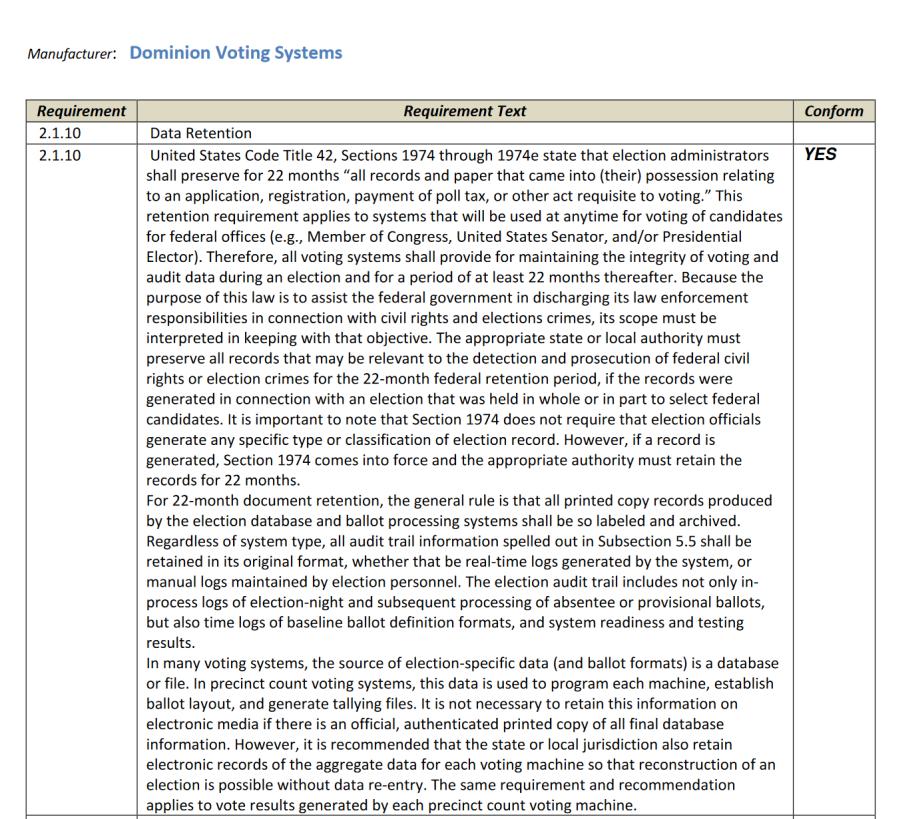
Oh, look! Someone photoshopped some highlights onto this screenshot from the compliance review:

Can you imagine the “burning Hindenburg performance” that Giuliani or Powell would have made if some awake and aware clued-in journalist had started bulldogging questions like, “how do you hypothesize they defeated the configuration controls documented in the device?”
Here’s some system architecture stuff from Dominion [dominion]
I’m just including that pro forma – any security analyst worth a pinch of sand would have been looking at the audit capabilities of the system, and wouldn’t it have been a fine thing indeed if some journalist had said:
Journalist: “Mr Giuliani, the voting machines you are talking about – all the vendors are required to meet certain audit trail capabilities, as part of the jurisdiction’s purchasing decision to use a particular voting machine for federal offices. Are you claiming that a couple of election workers were able to tamper undetectably with an audit trail that is, by definition, designed to make tampering detectable?”
I am aware that I am flogging a dead horse, here. Giuliani has since admitted that he outright made up that stuff about USB ports being passed around, and Powell has since admitted more or less to being a complete wackaloon – or, at least, meeting or exceeding the minimal amount of wackaloonery to be considered a wackaloon. Giuliani and Powell are going to wind up broke and derelict, given the huge amount of damage their knowing lies inflicted on voting volunteers, voting machine vendors, and the cost of many re-counts that they knew would not find anything.
What bothers me more than that a couple of loose nut has-beens have sunk themselves, is that the media couldn’t be arsed to do some basic research and shut that shit down. If you think back to the reporting about all the election chicanery, most of what we got was: “another Trump lawsuit was dismissed by ${Judge}” and that’s … it? What questions did the judge ask? What expertise did the judge bring to the table? Who did the research for the judge? If I can get a bee in my bonnet and dig up the Dominion system architecture in less than 10 minutes, and understand it in under 45 minutes, why couldn’t one of the media darlings’ assistants be arsed to do likewise? If I were a “journalist” I’d ask a rhetorical question like, “can it be possible that today’s journalists are a bunch of ignoramuses who think that reading and copy/pasting from Twitter is the whole of ‘journalism’?” The whole thing is a shameful shit-show and that’s why I haven’t been able to think about it. A plague on all their houses.

Also: I built a custom sled for my table saw and bolted the Dell computer to it, then sawed through both sides (power supply hard drives, everything!) at the precise, desired, angle. Wow, was that loud! even wearing hearing protection and a face-shield, it was quite a process. Then, the pieces were carefully hung on very thin stainless steel threads, from the ceiling of my studio. The rest was just setting up lights and a motion trigger, then doing a few cuts through where the PC used to be.

did “tardis” really need to be in that code?
btw, brilliant photo, moreso with the story behind it
I wrote basically this whole long response to the first few paragraphs of your post. Sorry about that.
Donald Trump does not make me angry to think about. If there are still historians and political scientists in 50 years, I suspect he’ll be regarded as something of a canary in a coal mine. There used to be political structures and systems that functioned to prevent people like Trump from taking power. Not evil people, not greedy or corrupt people – those were always allowed – the systems existed to prevent incompetent evil, greedy and corrupt people from taking office. Before Trump, a politician who made as many gaffes and mistakes, not to mention outright lies, as he did wouldn’t have been electable.
But those systems, guardrails, have been slowly dismantled on the political right. This was not an entirely intentional process, and Trump is the fruition of several different political projects colliding all at once:
Murdoch/Ailes’ determination to create a right wing thought-bubble universe for their audience so that another nixon impeachment couldn’t possibly happen.
The parasitic projects of the various social media companies determined to fragment and segment the population in order to maximize ‘engagement’, market share and advertiser spend.
The ever right-ward move of mainstream republican thought in order to capture more of the fringe audience – to replace their losses in popular support from their generally unpopular activities.
The Something Awful/Gamergate/4Chan-ization of modern discourse through advanced meme skills. Seriously, a disturbing amount of Trump’s most popular sayings and policies burbled up from those fever swamps. There’s nothing like an imageboard if you want a petri dish for incubating and forced-evolution of seductive bad ideas.
Trump’s brash crapulence and rank incompetence have bought the US some time, possibly several election cycles, to try to establish sane guardrails around their politicians. Imagine if he had not been the one to take the crown at the precise moment in time that he did. Trump is an excellent campaigner, at least for the base he courts. He’s an utter failure as a politician, probably for the same reasons that he was an utter failure as a businessman. His only major success was in pretending to be a mogul in a show written, scripted and edited by skilled people with an incentive to make him seem impressive. Everything else he’s tried on his own he has failed at. This is because he lacks any apparent ability to tunderstand what other people want – he may not even believe that they’re real. His idea of ‘making a deal’ is stiffing a drywall contractor on a final payment for work already completed. He does not know how to compromise, negotiate or function in the same rooms as people with independent goals of their own and any amount of relative power.
So any such people – he refused to work with. Trump’s ‘accomplishments’ as president are few in number and those few rightfully belong to other political actors who took advantage of his presidency to get things done that they wanted to do. The only real work he did in that role appeared to be (1) golfing and earning money by making his security detail pay their way in government lucre (2) preening before the cameras while being in rooms with real important folks (3) grifting with both hands, one in the pockets of his political base, and one in the pockets of wealthy foreign interests who would pay handsomely to stay at his properties in the hopes that he would do what they wanted with his political office. He had no other real projects. “Lock her up”? He forgot that one as soon as he was in the big chair. “Build the wall”? Did just enough to take a few photo-ops, then forgot the project completely.
Try a thought-experiment: imagine that someone with his kind of charisma but actual political skills had held the office. What couldn’t they have accomplished? The one project that Trump really cared about, stealing the 2020 election, he was unable to competently enact. Because he cannot tolerate being told ‘no’, he’s systematically filtered his underlings and accomplices ruthlessly against that one metric: “Will you tell Trump what he wants to hear?”. All the competence leached out of his pool of close supporters, replaced with paranoids, ignoramuses, lickspittles and fantasists. So long as the things they told Trump rubbed his ego the right way, they got to stick around.
That’s why his coup failed. People like Sydney Powell just didn’t know how to shut up – because the kinds of people who understand that, got shifted out of Trump’s orbit as soon as they said something he didn’t want to hear. The basic Trumpist coup plot goes like this:
(1) Lose election
(2) Supporters start making various noises about the ways the election was “stolen”. This playbook written by Roger Stone (see also: brook’s brothers riot)
(3) People who hear enough of (2) start to think “well, lots of people are talking about this, so there has to be something to it. No smoke without fire, right?”
(4) If there are enough (3), then politicians who generally support Trump become more amenable to taking unusual actions (replacing electors, ‘auditing’ vote counts)
(5) Enough disruption happens to the electoral process, and enough of the public are at (3) that the cowards in Congress feel bold enough to take unprecedented action to keep their guy in the big chair.
(6) Trump’s tame supreme court majority sees (2),(3),(4) and (5) and reprises their decision in 2000 and declares Trump the winner by judicial fiat. Enough politicians are at (5) that they don’t take action to resist (6).
But trump fucked up (2) really bad. His coterie of supporters was so packed full of loons and weirdos that their efforts to spread FUD about the election results were laughable. Sure, the trump faithful always sucked it up, but they couldn’t get a single court to entertain their arguments. Not enough people bought in for enough politicians to be willing to take the risk of appointing Trump to the presidency, and the actual voting results were allowed to stand. The tame monkeys on the supreme court would have happily installed trump, I think – but they’re also basically debate-club nerds at heart. They can’t completely ignore the record at the trial court, much as they’d like to, and since Trump’s teams of hand-selected-for-incompetence lawyers couldn’t make a good foundation, the Supremes simply declined to engage with it.
It didn’t have to happen this way. If you replaced Trump with someone actually willing to work with subordinates and sacrifice short-term gratification for a long-term goal, they could have actually *planned* for this election. They could have put the right kinds of people into the right kinds of places to make (2) much more effective and much less silly. Nobody would have made public claims about Hugo Chavez, for a start. But since Trump would systematically eliminate any subordinate who might have warned him that the election wasn’t as much of a lock as his ego demanded, he couldn’t plan for failure. A competent Fascist could have had people in place: suborned attorneys general/secretaries of state. Suborned polling supervisors prepared with realistic lies. Street teams of brownshirts to intimidate likely (brown/black) opposition voters from casting their ballots. Make the kinds of deals with Federal politicians that might make them willing to take a few risks to support Der Fuhrer if an electoral college needs to be brought back into line. Trump could do none of that, and we should all be quite thankful for his incompetence.
As for the meat of your post:
I think quite a few journalists did actually address the technical aspects of the various absurd vote-tampering claims. But it just gets lost in the chaff, also the more time you spend rebutting a false argument, the more people you expose to that false argument. There’s diminishing returns here. It’s not as if the whole nation is going to be watching one single interaction between Sydney Powell and a prepared interviewer, and even if there were – it wouldn’t help. These people have no memory for criticism and no shame at all about repeating a debunked argument to the next audience. See also: creationists. The detailed refutations of the arguments made by the pro-trump lawyers exist and were published, but anyone who was going to read those refutations likely already disbelieved the Trump lawyers.
Last:
Tablesaw? Ouch! I would have suggested a large vertical band-saw with a metal-cutting blade. Still, it’s a really great photo.
“I’m going to guess that no journalist appears to have asked that because journalists appear to generally be lazy, ignorant hacks who don’t do their basic research”
Every time I see an article / bulletin about something I know about it’s error-strewn.
I was, back in the late ’90s, the only person who knew and understood the sequence of events that led to India and Pakistan accusing each other of having an agent in the small company where I worked. There was a brief but intense brouhaha which made a few front pages.
Nobody even approached the company to ask what happened.
@3 snarkhuntr
Luckily the idea of a really competent Fascist doesn’t seem to be possible. The level of egoism necessary for real Fascist rule preclude a level of awareness required for actual competence at running a large government. Fascism is a system of ruthless power seizing so a Fascist leader has to be very careful allowing competent people near him. The Fascists that seemed competent in Germany and Japan both inherited a well run military that became less effective the longer the Fascist party was in power.
I really wouldn’t expect a reporter to ask the election deniers highly technical questions. What I did expect and nobody did was to really determinedly ask them for evidence. Any hard evidence, not just vague claims. An organization with real evidence of voter fraud would be making much of the evidence public to force the government’s hand in doing something. It would be better to make evidence public and risk making prosecution hard then keep it secret because that would give a chance to reverse the election.
The thing you have to remember is that, as far as most people are concerned, computers are literally magic, and “hackers” are literally wizards. They just don’t think of computers and IT systems as machines that behave according to knowable rules.
Most journalists are not experts in any particular field, save how to write prose. If you have detailed knowledge in a field, reading about said field in the popular press sometimes can be infuriating. This is particularly true at the local level where time is in short supply, budgets are non-existent, and the journalist is pretty much doing it alone. Much of local news has turned into “news readers” who pass along press releases and marketing materials.
At one time, I was a competitive masters distance runner. I was interviewed by a journalist at the local newspaper regarding a major race in the city that features international talent. Really basic stuff went out the window, like the concept of “pace”. That has a very specific (and simple) definition to a racer: your velocity in minutes per mile (or per km). The journalist responded with “When I think of pace, I think of…” and rattled off something else. Well, I don’t care what you think of because that term has a very specific meaning in this context. Your job is not to confuse the subject, it’s to make it accessible to the uninitiated. And this is running. It doesn’t get much simpler. Don’t get me started when it comes to something in my profession.
So no, I am not surprised in the least that a journalist didn’t ask these questions. For that to happen, you’d need real journalists who have an adequate support system to spend the time and resources to dig into it. Maybe ProPublica, but certainly not the evening news.
@jimf:
Once at a dinner with a bunch of techies (I think there were: a microbiologist, a master brewer, me, an audio engineer, and a physicist) I commented on how journalists get everything wrong when they try to cover computer security. And, then, everyone else said how journalists get everything wrong when they try to cover their field, too. We briefly trashed journalists for being a bunch of hacks and concluded that they probably get EVERY field they cover more or less equally wrong – i.e.: the only thing they are good at is tracking who is dating which Kardashian.
Then, the physicist pointed out that, if a Kardashian were present at the dinner, they would probably be saying about how badly journalists cover Kardashian anthropology.
I wrote a bit about the sad case of Baltimore Police’s murder and cover-up of Freddie Gray [stderr]
At the time I remember thinking there were other unasked questions, such as “if video camera X was not working at the time of the incident, when did it stop working, and when did it start working again?” also “what maintenance operations took place regarding the cameras?” The news distillation process allows this sort of question to go unanswered, providing a sheltering shadow for lies and corruption.
To be fair to journalists, though, there are many who are not simply following and reporting on some important person’s twitter feed. For example, there is Justine Barron over at The Daily Beast, who is still doing extensive analysis and reporting on the security cameras that conveniently failed to capture important moments in Gray’s murder: [dailybeast] this is what I call “journalism” and it clearly shows that Barron spent many hours looking at and thinking about – and questioning – this stuff.
… journalists appear to generally be lazy, ignorant hacks who don’t do their basic research.
If you had to generate articles on the current farm bill, a bribery trial, a Chamber of Commerce luncheon/circle jerk, a factory shutdown, and a school shooting – all by 7 pm sharp! 1200 words max! – how much depth could you bring to each piece?
JM @ # 5: … a really competent Fascist doesn’t seem to be possible.
Several of the first generation – Mussolini, Hitler, Dollfuss, Franco, Salazar – did have the skills and patience to succeed enormously. If only the second in my list had continued to nibble instead of trying to gulp, all of Europe (at minimum) would be goose-stepping today.
Is this a potential security approach? Instead of having one system, you have twenty systems, all deliberately designed differently. That way, if one system if breached, the other nineteen are still safe and hopefully you detect the first breach before the next one happens.
GAS #1
“did “tardis” really need to be in that code?”
Yes. Yes it did. 😁
My first question in the Giuliani/Dominion contretemps would be, “Do Dominion voting machines even HAVE USB ports, and if so, why?”
If I was going to develop a super-secure voting machine, I would first develop a port that required a mechanically unique cable and a unique data protocol. I would give each cable a secure machine-readable-only ID and I would track each person such a cable was issued to, and I would encrypt that cable ID into every data transfer. I wouldn’t allow any other ports on my machines.
I certainly would not allow a five-buck thumb drive from Walgreens to talk to my machine.
I presume now you have heard about Mike ‘Pillow Guy’ Lindell’s amazing election spying drone. Which I think has been adequately dissected elsewhere. The first problem is: what does the drone contribute? As he describes it, a wi-fi sniffer logs names and MAC addresses at election sites. So why not have it run as an app on a smartphone? The whole thing of attaching it to a drone seems to be an unnecessary and problematic complication.
@11 Pierce R. Butler: Hitler is the perfect example of a Fascist who got lucky to inherit a good military. The German military had actually been preparing to fight WWII since WWI ended. They had been violating the peace treaty almost as soon as it was signed. They were just careful to keep things secret as long as inspectors were watching the military in Germany closely. Germany’s WWII weapons, the tank corp, the air force, all of it was in development before Hitler took power. It was pure luck that Hitler gained power in Germany at the same time as the military was ready to begin openly violating the terms of the treaty.
@15 Reginald Selkirk: Lindell’s device apparently only covers wifi, which makes it a toy. There are lots of other ways of communicating. Plus there is no guarantee that the subverted device will communicate during the voting period, it may have been set to switch some percent of votes ahead of time.
The point of the drone is that it’s expensive and flashy. Lindell can charge a much higher markup on a drone then on an application for a cell phone.
@17:
You may well be able to charge a higher *price* for a drone, but surely the *markup* is going to be potentially much higher for a software product. (Especially as the drone would have to contain equivalent software anyway…)
@14:
So you’ve just been undercut by every other vendor on the market who use COTS and have gone out of business?
#19
Are you familiar with the story of STUXNET and the Iranian uranium enrichment centrifuges?
The point that xohjoh2n is making at #19 is that the decision is made on a commercial basis, not an engineering basis. It doesn’t matter what the security implications are, because the commercial considerations are overriding. If you want to alter that, then you need to look at how these systems are procured before you can even start thinking about how they’re designed and implemented.
I know someone who developed a specialized piece of test equipment for computer networks. They put a standard motherboard in it, for economic reasons, but did not accommodate the USB ports through the back panel. Because COTS is so much cheaper.
moarscienceplz@#20:
Are you familiar with the story of STUXNET and the Iranian uranium enrichment centrifuges?
They also destroyed the civilian reaction at Bushehr. Well, “civilian” breeder reactor. But the damn thing is in the middle of a city.
@17/19:
The only surprise about that drone is that it doesn’t store its output in the blockchain as an AI NFT for maximum not-really-understanding-it nerd-bingo appeal.
JM @ # 16: It was pure luck that Hitler gained power in Germany at the same time as the military was ready to begin openly violating the terms of the treaty.
And it was the generals’ bad luck to have dumped on them a C-in-C who thought their successes came from his genius – and assumed both had no limits. If Hitler hadn’t declared war on the US, f’rinstance…
moarscienceplz@#14:
If I was going to develop a super-secure voting machine, I would first develop a port that required a mechanically unique cable and a unique data protocol. I would give each cable a secure machine-readable-only ID and I would track each person such a cable was issued to, and I would encrypt that cable ID into every data transfer. I wouldn’t allow any other ports on my machines.
I certainly would not allow a five-buck thumb drive from Walgreens to talk to my machine.
It’s an axiom of computer security that, since computers are embodied in hardware, physical access to the hardware substrate will always allow an attacker to bypass the upper layers. I think that’s a correct axiom, as do most of the old school thinkers on the topic (e.g.: Roger Schell wrote a great paper on subversion in 1976 [a good piece on Schell]) Of course there are things that can be done to harden hardware, such as weirdly layered chips NSA made for Clipper/Mykotronix, or hardened computers like the ones that lived in cases with water cooling and the CPU poured into a block of epoxy resin…
Given that hardware is hard and expensive to harden, it forces us to use software techniques. For example, when we built the NID (network intrusion detection device) at NFR, I compiled the kernel without USB drivers at all. So, someone could plug stuff into the port, but – so what? That’s good protection as long as your kernel is the kernel running on the hardware. So you go into the BIOS and set it to only boot from a specified drive. And the boot process can check for a specific drive geometry and type. But then the bad guy can simply pull the hard drive out, image it with an offline imager, and your kernel never gets to run to protect itself.
That, by the way, is what appears to have happened in Coffee County, Georgia: the republican goon squad led by Sidney Powell took the hard drive out of a voting machine, imaged it, and then (we are not sure) may have kept the machine, because those machines have multiple tamper-detection seals and once the case was opened, the integrity of the system would be zero, without a doubt. Again, journalists ought to be asking, “what was the final disposition of the voting machine? who has it? it’s stolen property, why hasn’t the state of Georgia done anything about that?” etc.
Since physical access is a trump card, so to speak, it’s reasonable that a vendor do whatever they can with the software option. That keeps costs down and future-proofs the technology. As Dunc pointed out – commercial considerations force this, because custom hardware would result in a voting machine that cost 5 times what a system built on off the shelf hardware would cost, and a company that came to market with a system 5 times more expensive would have to be 100 times better and there’s not a lot of improvement left to squeeze out in voting machines, which are, basically, just tabulators.
Oh, and PS – one thing that’s great for disabling USB ports is JB-weld. Just trowel it into the port with a dental pick. It can be bypassed by opening the case and rewiring the USB cabinet header, but presumably there would be tamper seals all over the case.
Like other engineers, I too have noticed the lack of technical knowledge in journalists and politicians. And even the general public.
The thing is, it is hard these days to be well versed in a large amount of fields even if you are interested in these things.
So while I’m reasonably well versed in computers (having run Linux and later FreeBSD exclusively on my machines since ’97) and can follow and agree with your assessments, I suspect that the general public would not.
Also, there has been a significant movement on the part of the authoritarians to discredit domain expertise and stymie knowledge transfer. Because it’s much easier to rule the masses if they can’t poke holes into your fancy stories meant to induce outrage rather than careful thought.
In fact I would say that what authoritarians fear most is people actually thinking about what authoritarians are selling.
The problem with any kind of voting machine is, it’s not universally-comprehensible in the same way as pencil and paper; and therefore, anti-democratic, because it limits the pool of potential election scrutineers.
You can study the engineering drawings (which naturally have to be published, because the workings of the democratic process are more important than any corporate right to secrecy) and the source code of any software running on the machines — but without the requisite knowledge, they won’t mean much. Unless you know, for example, that a faulty emitter decoupling capacitor can cause a transistor amplifier to have a much lower AC gain than expected, or that it’s fine not to do an SEC before an SBC if the only way to reach that point is by falling-through a BCC, you can easily miss something.
And even if you devoted your life to understanding intimately every hardware and software feature of an electronic voting machine, and even if you arranged to visit the place where they are stored between elections and experimented with one or more examples to satisfy yourself it behaved absolutely correctly, you still would not know, by the time Polling Day came around, that every voting machine conformed exactly to the mechanical and electrical specifications of the machines you had examined and was running the actual software you had tested.
You have no way to know, when you press the button for Candidate A, that the machine has recorded a voter for Candidate A. Even if it spits out a receipt saying you voted for Candidate A (which is potentially an incredibly dangerous thing; imagine a workplace telling employees that they will only be paid for the time taken out of their day attending a polling station on production of a receipt for the director’s preferred candidate) you still have no way to know your vote has not actually been recorded for Candidate B.
This isn’t a limitation of present-day technology, that we could one day invent a solution around — it’s a limitation of the universe.
The nearest thing I can think of would be a direct-recording, purely mechanical device using non-resettable counters with rows of numbered wheels, two or more for each candidate, and the whole thing in a transparent housing, so every moving part can be seen except the digit wheels themselves; which are surrounded internally by distorting lenses so you can see if they move, but not what digits they are showing, and covered externally by individual sliding shutters. Depressing the button adjacent to one of these counters retracts the shutter to display the count, advances it by one and then locks the mechanism up; requiring it to be reset for the next vote, using a Bowden cable connected to a trigger under control of the Presiding Officer, after the next voter has entered the polling booth. On the other side from the buttons is a hinged flap, with space on top for tamper-evident stickers bearing the names of the candidates for whom each button represents a vote; under the flap is a paper where the counter readings are recorded at the beginning of the polling day, and more distorting-lens material to prevent reading the initial counts through the transparent housing. You can verify the entire operation cycle as you cast your vote. The use of multiple counters per candidate means that anybody wanting to find out who you voted for needs to send in several goons immediately before you and as many immediately after you in order to see which counter changed — and all their votes will be counted. I would still hesitate to describe such a machine as “universally-comprehensible”, even although all the moving parts are big enough to see moving — and just because I can’t see a way to cheat with it, doesn’t mean there isn’t one.
By contrast, when you make a mark on a piece of paper next to Candidate A and place that actual piece of paper in a box, you can have a bit more confidence that it is going to be counted correctly. When you can volunteer to oversee the delivery of the sealed ballot boxes to the counting centre, you can have a bit more confidence. And when you know Candidate A themself — along with all the other candidates, none of whom trust each other as far as they could throw them — will be directly involved in the counting of those pieces of paper, you can have a bit more confidence still. The adversarial relationship between the people doing the counting means the only result on which they can ever possibly agree is the truth.
The democratic process is fundamentally too important to entrust to opaque machinery, and if doing it properly requires doing it by hand and slowly then that is time and effort well spent.
@29 bluerizlagirl: What you say has some merit but also largely doesn’t matter. The current voter fraud issue isn’t an honest issue. It isn’t caused by people with real questions about their vote. It’s mostly an intersection of two groups. The first are Trump cultists who believe that the election must have been fraudulent if Trump didn’t win. The second are politicians who know that Trump lost but are willing to raise the issue for their own political advantage. After that there are some grifters willing to run with it as long as it’s profitable and some anti-democratic party activists willing to run with it as long as they can use it as a weapon against Democrats.
The key thing is that none of these groups are really concerned with voter fraud or how secure the voting system is, they are concerned with the voting system producing results that show Trump won. No matter how secure and simple the voting system they would have the same issues. This is why they can raise more then 50 cases in court, lose every one for lack of evidence and still say that Trump should have won.