I guess it’s just part of the “political goon mindset” to want to be photographed standing in front of important-looking things. Donald Trump and his nachos, Kim Jong Un and his nuclear weapons explosive-lens carving CNC machine, and Rouhani by his breeder reactor control panel.
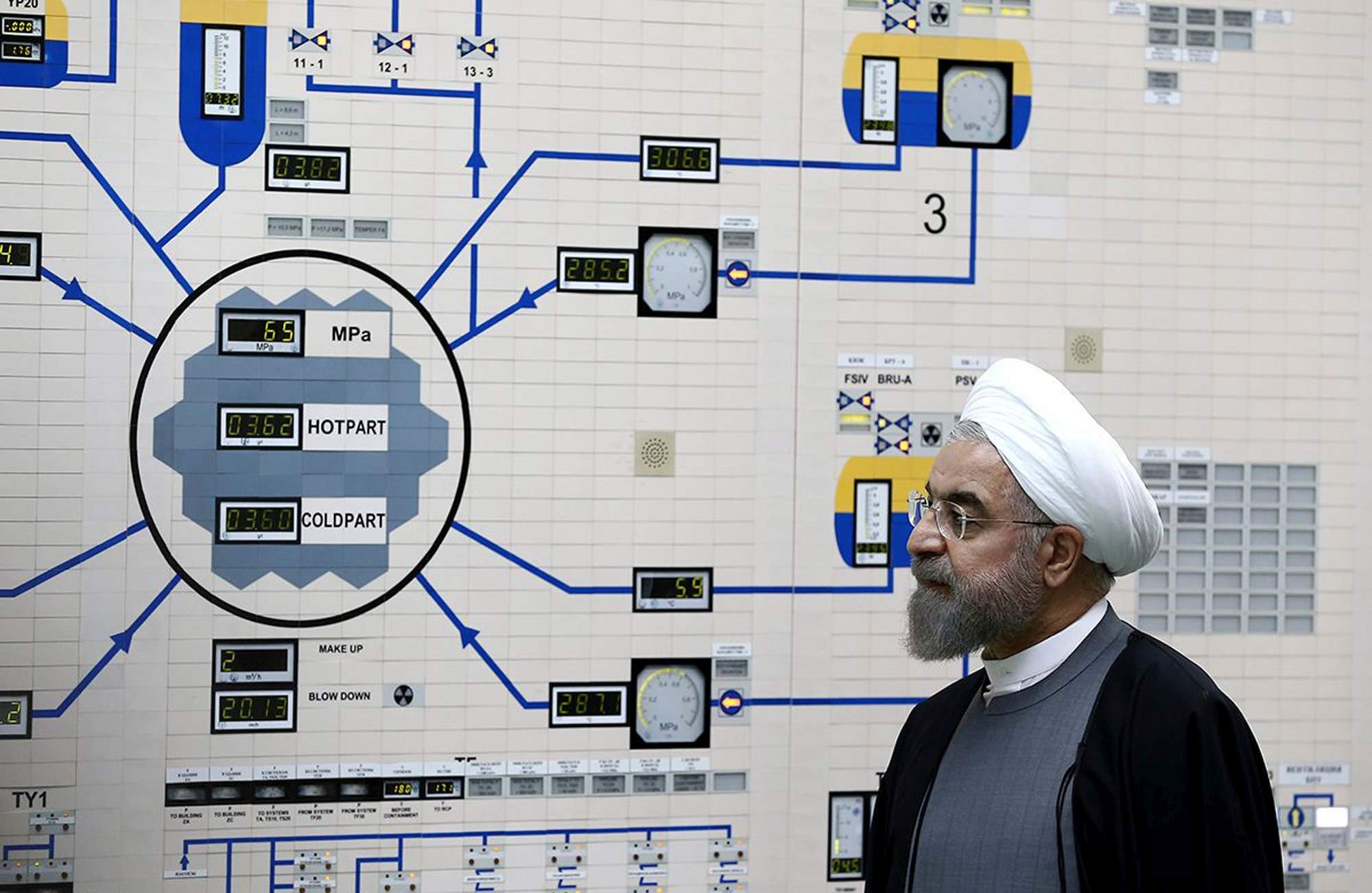
Normally I’d downsize the image substantially, except in this case you might want to blow it up and look at it more closely. Like the CIA analysts who are programming the next version of Stuxnet are doing.

In the right hand side of the picture above you can see the edge of a control panel – that’s the SCADA controls that drive the centrifuge cascade. And, not that anyone suspected otherwise for a second, those are definitely A. Q. Khan’s RP-1 centrifuge design. I’m not an expert in weapon development, but someone who is could confirm a lot of things from that little walkthrough. Think how much that photo-op cost Iran, in terms of effort and money spent.

What kind of CNC machine did you say that was, Kim? Have you kept the software patched? I sure hope it’s not on a network. Who’m I kidding? Of course it’s on a network. It’s probably running Windows, sucker.
At least it’s not as bad as these guys, who left the admin password on a post-it note on the console while they posed for a photo for failblog:

What I want to know is why they still have Internet Explorer on their systems. Geeze, are they running Windows XP? OH MY GOD it looks like they are!

I don’t want to appear to be encouraging dissention among the FTB ranks, but one of us has a lab full of giant spiders and sometimes posts photos of them. We all want to be sure that person does not accidentally include, in one of those photos, the SCADA interface for the control-flow that feeds those giant spiders, and the administrative password for the giant spider release trapdoor system. This is serious business, people: cyberwar is all fun and games until someone gets sucked dry.

Maybe they switched the labels around before taking the photo.
As for the giant spiders, I concur. They will not be ready for release until they’ve developed a proper taste for rich politicians and billionaires.
voyager@#1:
Maybe they switched the labels around before taking the photo.
Maybe, but that’d also be pretty obvious to an expert. “wait, why’s the haydiddlediddle connected to the oompawpaw?”
As for the giant spiders, I concur. They will not be ready for release until they’ve developed a proper taste for rich politicians and billionaires.
Now I feel like I should be contributing to the program!
I noticed this story: https://www.theguardian.com/world/2019/jun/23/us-launched-cyber-attack-on-iranian-rockets-and-missiles-reports
(Can’t take it at face value, it seems really stupid to burn an exploit)
@ 3 John Morales
(Can’t take it at face value, it seems really stupid to burn an exploit)
I agree; an article like that could cause Russia to waste vast resources, just because one cannot be sure it is not true.
But this is the USA. This is the country that was so proud of helping Boris Yeltin win an election that Time magazine gave them a cover story; this is the country were Madelaine Albright admits in front of a camera that sanctions killed 500,000 children in Iraq and says it was worth it. Discretion is not their middle name.
I have no way of checking the sources on this posting but
The CIA’s worst nightmare
This is not in the tradition of Enigma
John Morales@#3:
(Can’t take it at face value, it seems really stupid to burn an exploit)
They thought they were disrupting Iran’s military command/control in advance of airstrikes. So the US was ready to go and commit a bunch of war crimes, initiated a bunch of them, then de-conflicted instead of going through with the strike. My assumption is that it’s a matter of that the left hand and the right hand did not coordinate properly. I have a posting in queue about this for tomorrow evening.
You can be sure there are some cyber”warriors” who are deeply pissed off about this – they lost some of their favorite exploits and burned a few operations, but they have an infinite budget and they’ll just develop more. Meanwhile, the Russians will probably help the Iranians figure out what tools were used, and in a year we’ll see them released in a Vault-7 style wad to make NSA look bad. That, or cybercommand’s hacking tools will show up in US government networks; that’s how the Russians play this game.
jrkrideau@#4:
I have no way of checking the sources on this posting but
The CIA’s worst nightmare
That is substantially correct. Multiple opposition intelligence forces have been able to get inside the US Government’s systems and learn a great deal about what the US intelligence community is up to. Not too long after the Office of Personnel Management hack, China rolled up an entire in-country CIA network and presumably rendered the agents as involuntary organ donors (i.e.: sold them back to Americans as parts) It was a catastrophic defeat but the US would have to confront its bad security practices in order to prevent something like that happening again, and inter-agency cooperation is still harder than a whitewash.
The US intelligence community is leaking like a paper cup right now, and they have been told by lots of savvy people that the problem is going to get worse, not better.
This is not in the tradition of Enigma
The Brits sensibly worried about bombs landing on Bletchley Park and did not look far forward to the consequences of sharing information with the Americans. The WWII cooperation regime established between US, British, and Canadian intelligence turned out to have a “too many cooks in the kitchen” problem and was fairly quickly compromised by the KGB. in ways that were predictable and predicted.
Here’s another data-point: the highly oppositional cold-war model was a moderate failure, but relied on knowing who the enemy was. In other words, they knew enough to look for KGB spies and it was pretty straightforward cat and mouse. When the Chinese began to come up, around the same time as the post-Soviet KGB was let off its leash by Putin, the US literally had no strategy for what to do. They still don’t! The fucking idiots are still pushing things into the cloud and to beltway bandits, in spite of the rather obvious fact that only increases the leak-rate. “OH NOES WHAT DO WE DO!?” I know, let’s outsource harder because that way we’re less likely to have incompetent government employees trying to deal with the situation. Meanwhile, let’s outsource to the lowest bidder and expect the best results.
Let me explain a little more, since the whole OPM disaster has been described only obliquely by the US Government. In a nutshell: OPM had consistent security problems with their systems and networks and was written up as failing to adequately secure their systems by auditors for years. Basically, their attitude was “we don’t have the time or money to do this right” so they just let things sit: out of date systems, poor system security practices, inadequate logging and general sloppiness. That’s par for a government agency and OPM appears to have concluded that their data didn’t matter, so – whatever.
Naturally, it mattered.
The quintessential intelligence operation is one where you are able to collate data and form an improved picture from multiple sources. China had already been working hard to figure out what CIA activities in their country looked like, but the OPM databases had confirmatory information all over it. For example, in the OPM database there were fields that listed an agency employer code, pay grade, and currency of highest clearance level that the employee held. It was not as though the “employer agency” field said “CIA” or NSA – but when you know that Fred Jones works for CIA and is a GS-12, and you look in the database and there is Fred Jones, GS-12, working for “Agency #129” you don’t need a whole busload of data analysts to extract the CIA’s payroll from the database. And the NSA’s, and, and. OPM also had things like immunity history (“oh look everyone who gets Zika shots must be going to Brazil!”)
The OPM breach provided every other intelligence agency in the world a complete map of the US intelligence community (all other federal agencies, also) – through time – want to see if the CIA is staffing up? Look at employee terminations versus hires. Want to know their budget? Estimate based on how many employees at what pay grades.
Apparently there was even travel data: what CIA torturer spent 3 months at “Facility #1872 in Thailand in the summer of 2002”? Was Haspel, G, there too?
OPM was computer security incompetence on the order of “hey let’s attack Russia, on foot, and only bring our summer campaigning uniforms.”
PS – friends of mine who were involved in the breach analysis said cheerful things like “no matter how bad you think it is, it’s worse than that.”
@ 7 Marcus
God, I knew the data breach was bad but had no idea how bad. What was the OPM’s definition of security. Lock the door and turn off the lights when you leave the office?
I am a industrial psychologist by training but I’d be itching to get digging to a data trove like that. I, once, was on a team helping a government department get ready for a human rights compliance audit by the Auditor General and it is absolutely amazing what you can get out of personnel files.
This is not in the tradition of Enigma
The Brits sensibly worried about bombs landing on Bletchley Park
Very true but that was not the point I was trying to make. The point was that no one who knew about Enigma ever spoke about it to “anyone” until the 1970’s.
You never tell anyone what was done. That was the same point John Morales was making.
Bletchley Park heroes went to their graves with their families thinking that mommy or daddy spent the war as a clerk in the Civil Service. One of the reasons Alan Turing died, as he did, was because neither he nor HM Gov’t would admit Enigma existed.
I heard an interview with what be one of the last survivors of Bletchley Park on CBC Radio last year. It was the first time she had ever talked about her experiences and she said it still made her nervous.
The same thing applied to the naval code breakers in WWI. To reveal to the world that the RN had broken German naval codes could give an advantage to an enemy in the next conflict.
The British, BTW, were livid at the attack on Admiral Yamamoto. If one interpreted the event correctly it showed that Japanese Imperial Navy codes had been broken. Lucky, they missed the significance of attack.
I think the UK Gov’t finally admitted Enigma existed in the 1970’s because new computer-driven technologies meant that the secret no longer had any real value.
@6:
“The Soviets are our adversary. Our enemy is the Navy.”
(And googling to provide the precise form of that quote shows an *awful* lot of more recent variations on the theme by US politicians. What *ought* to have been satire is now apparently mainstream…)
Well, at the time we were still selling it for a lot of money to other countries as a super-secure system that had never been broken…