I ordered a tactical defense knife (“the perfect tool for women”) [stderr] so I can use it for some test-cutting. I’m not sure where I’ll go with this, but I am probably too busy/lazy to make my own tactical llap goch sgean dgu to compare against, so I may have to use my Vietnam War-era Gerber MK I.
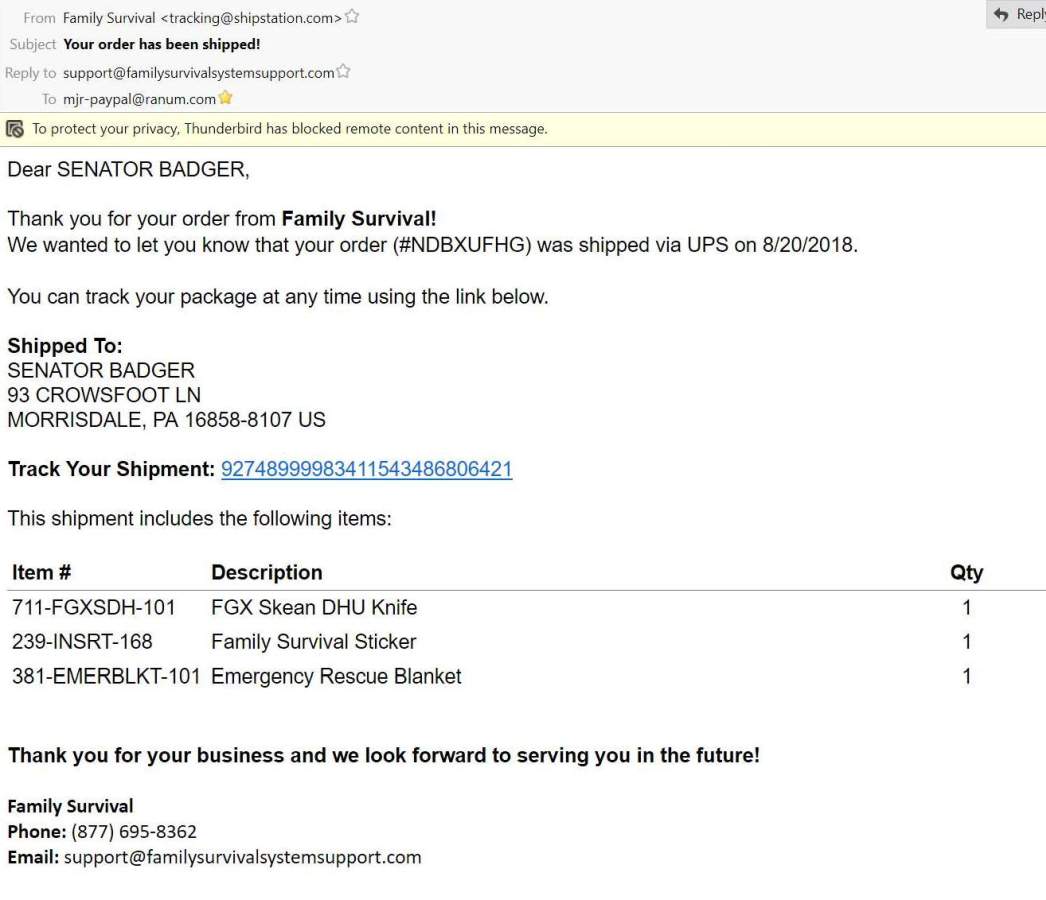
It sounds like I am fortunate – not only am I going to get the knife, they’re giving me a mylar sheet and a sticker!
Maybe I can find an old Ginsu on ebay and compare the tactical defense knife against that monstrosity from the past.
Anyhow, that’s not what I wanted to talk about today. Notice the name I bought the knife under? It’s an old habit from decades of doing computer security – a “honeytoken” – a value that I control being inserted into someone else’s database and I can watch where it crops up, thereafter. Some people call this a “data canary” technique.
Back in the late 80s I signed my cat (Dr Miso Katz) up for a subscription to a certain magazine, and it became a fascinating exercise to see where that name kept cropping up, again and again. In the 90s I hit upon putting a certain user in a system’s password file, and setting up an alarm in the user’s .profile so that I’d be notified (and everything they did, recorded) if that user ever logged in. That alarm “dinged” remarkably quickly, and that was how I discovered that a certain organization had been compromised and didn’t know it, yet. (It also served as a benchmark for the speed of the hackers’ password cracking system and size of their database). Many years later, I convinced one of my consulting clients to add a customer named “Fred Fishlips” to their database, and set Fred up with a gmail account that forwarded to their security ops center, and a few other things like that. A year afterward I got a call at 3:00am asking me if I could get on an airplane out that night, because Fred Fishlips was getting email from a spammer. Fortunately, they had also done another thing I suggested, namely set up a process that updated Fred Fishlips’ birthday to ${today} every night. That way if they ever found a copy of their customer database on pastebin, they could tell what day it had left the building. These little things can save a huge amount of diagnostic time in an emergency, and it’s a simple outcome of an exercise that I tried to teach for decades:
If you are responsible for security
- Ask yourself “what are the bad things that should not happen?”
- Then ask yourself “what would it look like if those things that should not happen are, in fact, happening?”
- Ask, “what can I put in place to notify me if things look like ‘that thing that should not happen’ just happened?”
- Lastly, ask, “when all that happens, what information about the event will I wish that I had?”
If you know Fred Fishlips is not a real user and nobody ever should be accessing that account’s information, you can have your edge firewall look for the string “Fishlips” and ding if that pattern leaves the network. Well, now, if you had that in place and I hadn’t changed the name to protect the honeytoken, your alarms would all be ringing now that you’ve read this blog-posting. I have been using Fred Fishlips as an example for a long time, and I was teaching a class on honeypots at SANS in Boston, when someone trolled me, hard: I said ‘Fred Fishlips’ and a guy in the class replied, “yes?” He insisted, for a few moments, that his name was really Fred Fishlips and I started apologizing and we all cracked up laughing.
I’ve never had access to a copy of Palantir (it’s very expensive!) but I used to occasionally day-dream about building an evolutionary contact-map of who sells which of my various IDs to what marketing company. Sometime around 1996 I started signing up for conferences using traceable or ridiculous corporate identities. My most successful, to date, was “Heavy Weapons Research Division, Bellwether Farm” which I enrolled at an RSA Conference around 1999. I started getting messages under that title nearly immediately. After a year, I started getting invitations to attend small arms sales conferences and I was so amused I actually emailed the marketing contact there with a message: “Heavy Weapons Research, not Small Arms.” Then, I got 2 flyers for a conference of artillery munitions providers. Since Bellwether Farm has no End User Certificate, and artillery is expensive stuff, I have refrained from pursuing and of that any further. Though it would make a fun retirement project to try to get an invitation to attend some arms dealer conferences and publish what they’re about. I keynoted a computer security conference in Qatar, back in 200?5, and it was co-morbid with another security conference featuring crowd control and counter-insurgency gear. I checked out the show floor and it was depressing as hell. Arms dealers’ conferences are just like everyone else’s: just a bunch of sales guys who want to send you their brochures.
One of my more interesting canary accounts was my old ranum.com!mjr-paypal account. I have an Ebay account and a paypal account that are different (and have different passwords) so I can detect if either of those services customer-base gets used for spamming. I used my accounts for a long time and about 2 years ago I started getting a lot of spam on the mjr-paypal account. My conclusion was that a certain seller who was offering fairly low-cost items of a certain type was selling their customer-list. I use many email accounts for many websites (and all have different passwords) and I watch the ranum.com server logs for login attempts on them – that’s a good early-warning system that a site has been compromised, and it neatly tells you which.
Dr. Miso Katz’ last surface mail credit card offer was received in 2002.

Wow, holy moley! Did you know they still make Ginsu knives? And they’ve branched out to offer a wide variety of blade shapes, etc. I just ebay’d up a Ginsu steak knife that looks to be about the same length as the tactical thingie.
Now I want to make a damascus high carbon steel Ginsu-inspired blade. My sense of humor is bad for me, I know.
“Going to odd conferences and doing reviews” would make a pretty cool blog-site for a retired and bored person. I hate travel too much, after too many airports and hotel dinners, or I’d seriously think about doing it.
My favorite crossed conference was the time Secure360 was held at the same hotel as the Society Of Forensic Toxicologists’ annual meeting. I actually attended a couple of their talks, and bought a kickass polo shirt, black cotton with a skull and crossbones and “Society of Forensic Toxicologists.” They were a pretty cool bunch of people, very enthusiastic about their craft and not at all creepy.
For a number of years I used “Bellwether Farm” as a designation for my farm, on any business reply forms. That was based on Connie Willis’ excellent book, Bellwether. [wc]

Is that a small knife, or an adhesive label?
LOL! Well done, Senator Badger! May you receive a lot of interesting spam.
The worst place I got spam from was GoDaddy. I mistakenly followed the advice of someone who was re-writing my website, and got a couple of extra domain names from them to point at my website. What a mistake that was… within a week I was not only getting daily emails from people who wanted to help me with my “new site”, I was getting daily **phone calls**. I allowed the domain names to expire the first year and will never do business with GoDaddy again, and it sure made me jumpy about working with other companies!
Reginald Selkirk@#1:
Is that a small knife, or an adhesive label?
I assume it’s an ad for their products, such as I might stick on my suitcase if I wanted to ensure it was searched by TSA.
kestrel@#2:
got a couple of extra domain names from them to point at my website
Yeah, they are one of those businesses that built their value by inflating their customer-list and then selling it to marketing companies (see also: RSADSI, Facebook…)
I didn’t even get into the fun aspects of signing into conferences and giving someone else’s address. I know someone who used to attend the AVN (Adult Video News) which was conveniently held in Vegas the same days as Networld+Interop, and he’d give the name and office address of a certain annoying FBI Supervisory Special Agent.
I like this one. That was funny. Your invented names are cool.
Such a stunt would be impossible where I live. Latvians never trust each other. Delivery guys or post workers never give me any packages without taking a look at my passport and making sure that my name matches that which is written on the package. Compare that with Germany where instead I usually picked my packages from my neighbors. Germans seemed to trust each other a lot more, and post workers just assumed that leaving a package somewhere near the right building will result in the right recipient getting it at the end. Latvian post workers, instead, believe that even a family member might steal a package if it isn’t personally given to the intended recipient.
Usually reading your blog makes me depressed and pessimistic about humanity’s future. This time, however, I kept laughing while reading this. Thank you! That was fun.
@#2
Ouch! That’s bad.
Regarding phone calls from marketing guys, if the call happens during a moment when I have nothing better to do (while I’m commuting, for example), I sometimes use these calls as an opportunity to mock and make fun of the poor person who was unlucky to call my number. Where I live, we don’t get any robocalls, it’s always a human being calling, so that works here. Marketing people usually attempt to follow their scripts, which is why I start by interrupting or even totally breaking the script. I ask them uncomfortable questions about their product (the kind of questions that would require an honest person to admit that their product is a piece of crap). When they try to answer me, I enjoy listening them squirm. If there are any weak points in the replies I get, I attack those, and move on to outright mocking them. This can be really fun (well, I can be mean sometimes). The key to successfully pulling this off is controlling the direction of the conversation and making the other person unable to stick to their script (they will try very hard to do that). It’s also necessary to corner them in such a way that they start feeling uncomfortable. This can be achieved in various ways, for example, if they accidentally say something careless, I can ask, “Did you just insult me?” And then the fun begins. Possibilities are literally endless here.
Most of the time, I must be polite during my everyday conversations. After all, I don’t want to mistreat somebody who hasn’t done anything to deserve my wrath. Marketing people are one of the rare acceptable targets against whom I can practice my verbal abuse skills. I can also make fun of them or just confuse them. I perceive this as a game.
Those were the good ole’ days; pets with credit.
I came across http://canarytokens.org/ which seems like an easy way to get into using honeytokens.
leva:
The only problem is these are typically desperate people doing a “shit job” that they undoubtedly hate. I would have trouble being too cruel.
Now…obvious criminal scammers (the Nigerian Finance Ministers) are fair game.
Used to do the same myself when entering “competitions” at trade shows. All I would do would be a slight mistake in spelling of my name or add an A or B after my address. Mail would still arrive, and even in the days of clunky Databases (think Dataflex, DBIV, etc) it was amazing how fast the spam arrived.
bliving@#7:
Those were the good ole’ days; pets with credit.
I keep getting those “your business is pre-approved for up to $250,000” and I wonder if my horse P-nut would like to complete his degree in Equine Massage and hang out his shingle.
(I actually did research getting him a PhD from a degree mill that offered alternative medicine. I thought a certificate would look nice hanging up in the barn. But they wanted $500 and P-nut would have preferred $500 worth of carrots so … he remains uneducated.)
DavidinOz@#9:
Mail would still arrive, and even in the days of clunky Databases (think Dataflex, DBIV, etc) it was amazing how fast the spam arrived.
The most annoying thing is that the FTC threw the citizens under the bus when they wrote the spam laws (which are never enforced anyway) by allowing an automatic opt-in for anyone a business has done business with. Naturally, they all lie anyway, but even the reputable ones get the attendee list from conferences and treat that as opting in.
And since I’m on that topic, the NSA and the phone companies are perfectly capable of identifying who is spamming and robocalling. They could identify every single goddamned one. It’s actually really easy (just look at claimed call origination patterns clustered by recipient) But they’re too busy reading your email to make sure you don’t say “allahu akbar” or “I want to join ISIS” or anything like that.
bmiller@#8:
The only problem is these are typically desperate people doing a “shit job” that they undoubtedly hate. I would have trouble being too cruel.
I concur. I stopped being grumpy with them, and now I just hang up immediately so they don’t waste any time and breath and can get on to their next call.
Now…obvious criminal scammers (the Nigerian Finance Ministers) are fair game.
Oh, I have done some really evil things to Nigerian spammers. I don’t know if I should post about that, because you all will realize what a horrible human being I am. I’ll think about it.
There is another horrible idea I had back in 2003 when the NSA spying story was starting to leak out. I’ve kept quiet about that because I don’t want someone to do it and then I have the national security state wondering why I decided to switch sides on them late in my career. ;)
In the early days of the “Moral Majority”, I accepted an offer of free sample newsletters under the name “L. Mergantry” and was utterly astonished to receive the newsletters, a few months of MM $olicitations, and … nothing else.
Later, particularly as he went through near-bankruptcy, I learned that Jerry Falwell Sr. was the least money-hungry/skilled of all the megatelevangelists[1], so that unexpected restraint made a little more sense.
[1]Fame and (proximity to, at least) power, now, that’s another story[2].
[2]Jerry Jr wants those too, but he also makes up for his daddy’s negligence by turning “Liberty” “University” into a major Mammon machine of the online worthless-degree-mill type which sucks up over half a billion bucks/yr in federally subsidized tuition payments alone[3].
[3]How much of that sticks to JJ’s fingers remains a need-to-know Top Top Sekrit.
I have been thinking about this one. A lot, in fact. I know that I’m probably not hurting my real target. If the spamming company is paying their workers at least the minimum wage for the time they spend working, then the one I’m hurting is the company (who get to make fewer calls, because I trolled them and wasted their employee’s time). However, some companies abuse legal loopholes that allow them to pay their workers based on how many successful sales they make. This way I’m hurting the employee who didn’t deserve it. And I also fail to hurt the company that was my real intended target. So, yes, I see a problem here.
Anyway, let’s begin with the fact that I’m only trolling snake oil salesmen (last time I played this game, I was being offered alternative medicine). I’m not trolling people who offer me legitimate stuff that can actually be useful for somebody. In these cases, I simply say “no,” and end the phone call immediately.
In general, I’m sympathetic towards desperate and impoverished people who are forced to take shitty jobs. They do this only because they have little choice about employment options. That being said, even a desperate person ought to think about how their actions are hurting others. Impoverished and hungry people would do less harm by shoplifting food in grocery stores compared to making phone calls and attempting to sell snake oil (for example, alternative medicine that I already mentioned earlier). Let’s assume that one snake oil salesman can make at least 60 phone calls during an hour. That means they have already annoyed 60 people who were forced to waste a bit of their time. Moreover, assuming the salesman successfully sells some snake oil, they have just scammed some unfortunate person out of their money, and possibly, also given them false hopes and prevented this person from seeking an effective solution to their problem. Compared to this, I’d rather pay larger grocery bills because of hungry shoplifters. And I’m using shoplifting as an extreme example here. Usually unemployed people actually have some choice about where to work. Sure, there are only a few options, and all of them suck, but some jobs are worse than others. Choosing a job which directly harms other people is a bad choice.
I wanna know. I wanna know. I wanna know. Hinting that you have a fun story and then not telling it is like teasing a dog with a steak and then pulling it away at the last moment when the dog is about to bite in it. (Hmm, you did say that you can behave like a horrible human being.) Still, not telling something after you have piqued somebody’s curiosity is not nice.
Also, I just realized what my curiosity tells about me. Here I am, sitting behind a computer screen, laughing evilly while reading about how some poor souls got trolled really hard. Oh well, I’m not exactly trying to hide the fact that I can be mean.
You aren’t telling this one either, aren’t you?
Marcus #11, that is a real problem for me as my daughter and her husband both work for part of the Oz Police State. My daughter asked me to remove pictures of my grandchildren from Facebook. My daughter does not have a Facebook account. How does she know those photos are there? (Rhetorical question).
ROFLMAO! I have deliberately or accidentally done most of this, including having a cat with a superb credit rating and a combat history.
I started ordering things using my cat’s name, let’s call him “Fred”, to track junk mail. At the time I was living with my elderly parents, and my dad started doing the same. “Fred” bought everything that was mail order.
Somehow, somewhere, the information streams crossed. Fred became a military vet, and a computer whiz, with our combined incomes (which was pretty decent) and purchase histories. I was buying a replacement vehicle and asked the sales manager, a personal friend, to run a credit check on “Fred” … he refused until I explained that Fred was a cat (and by that time, defunct). He ran the credit check and Fred could have walked out with the most expensive car on the lot with a signature loan! (I realized later that Fred and I were being confused with a high-paid engineer with the same last name and my initials when I got junk mail every time he got a patent!)
Fred could have been a member in good standing in the VFW and American Legion (my dad) and had any number of computer knowledge certificates.