There’s a small bit of kerfuffle around the new iPhone facial recognition feature.
Personally, I’m more worried about what sampling the camera all the time is going to do to battery life.
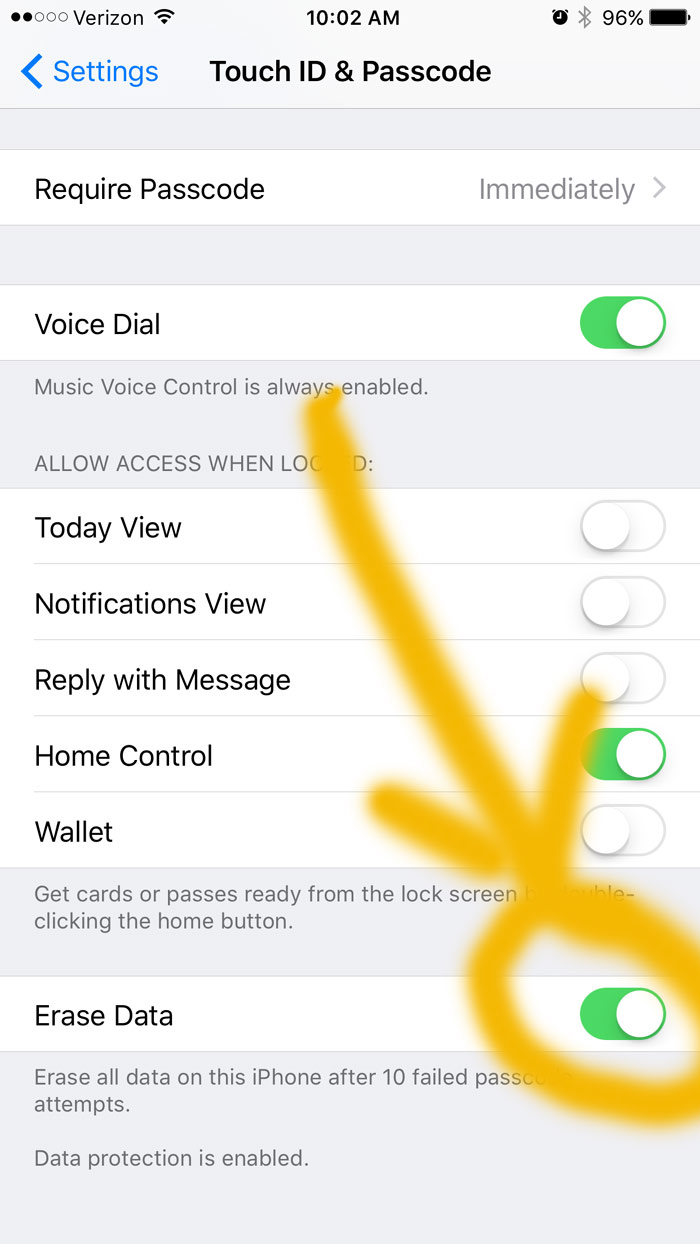
 Whenever crossing borders or traveling, you should, as a matter of course, change your device-lock policy. Whenever I am going to an airport, I always dismount my encrypted hard drive partitions and change my phone unlock policy; I do this for the good of law enforcement and the intelligence community, in order to help encourage them to be honest.
Whenever crossing borders or traveling, you should, as a matter of course, change your device-lock policy. Whenever I am going to an airport, I always dismount my encrypted hard drive partitions and change my phone unlock policy; I do this for the good of law enforcement and the intelligence community, in order to help encourage them to be honest.
If Apple ever ships an iOS version that doesn’t allow you to turn off the easy unlock, then you know they’re owned. I suspect it’s already much worse than we think; iCloud is a great big wad of bits hanging out there, ripe for offline attacks, and there are techniques for embedding law enforcement access to keys into public key systems (the approach in the old Clipper chip) – the only reason that they want your phone right now is because if you’re there they can say you looked suspicious or whatever, and they can pressure you by grabbing your phone, searching your anus, and making you miss getting to wherever you were going.

[source]
Need I mention: don’t use the PIN for your ATM, and use a minimum 6-char PIN. iOS is suspiciously eager to let you use a 4-char PIN: don’t do that, it only takes 1,000 tries to break one of those – fewer if they call your bank and get your ATM PIN.
You should understand your security of your device well enough to be able to rattle it off: “Officer Porkbloat, please do not fiddle with that – it has a long PIN, thumbprint is disabled, and wipe is set. You’ll make me lose my data and that’ll waste both our time – why don’t you subpoena it or just ask me nicely and tell me what you’re looking for and then we can all save money on lawyers?”
If you’re really paranoid (you should be!) don’t enter your PIN in an airport – you’re almost certainly on camera.

Hi Marcus. Wouldn’t it be 10,000 attempts to crack a 4-char PIN? Or am I missing something?
Is there no self-destruct of the incendiary kind? I figure if I ever do want to yield to paranoia unbefitting of my rank, that’s the route I’d go.* Plus, if my smartphone were to explode in an airport that would make the security guard responsible (a.k.a. ‘the terrorist’). I, on the other hand, would have the perfect excuse to sue airport security as well as severe burns.
Come to think of it, I want this feature now so I can switch it on already. I wouldn’t want it for my laptop, though. I actually like laptops.
*Trying to steal blurry pictures of my new nightstand? No? Well, that’s all you’ll find on my device. Now pay the price for your intrusion!
On the topic of phone access in general:
If we assume manufacturers have successfully been pressured into incorporating backdoors into their devices, wouldn’t it be much easier to access smartphones wirelessly? E.g. have a little device that connects to the phone, says some magic word and gets full access. It could then, for example, decide to unlock the phone or even browse or copy all it’s data to be viewed on the device, rather than the phone. In theory you wouldn’t even need to let the phone owner know about this. Just clone and ‘investigate’ everyone’s phone as they walk through the airport securityscanner. If the reader works on mobile frequencies people wouldn’t even be able to block it by switching off wireless or bluetooth connections.
That way mobile phones could still have all the security features that make it hard to crack, but also fold instantly (and quietly) if a transmitter nearby says, ‘Hi, I’m the government and I would like to search you.’ , in just the right tone of voice. Noone would even have to know about this. At least not until the inevitable leak of classified files and / or when the readers turn up on the black market, ebay or amazon. (Customers also bought: Credit card duplicator, PIN-stealer, Bag With Dollar-Sign (XXL))
Is there no self-destruct of the incendiary kind? I figure if I ever do want to yield to paranoia unbefitting of my rank, that’s the route I’d go.
I believe the old-school CIA trick (which failed badly in Iran during the uprising that led to the hostage crisis) was pre-positioned thermite charges. Thermite’s pretty easy – I could whip you up a small batch pretty quick – but it’s devilish hard to ignite and it’s nowhere near as powerful as they portray it to be on TV. You’d probably be better off hauling an oxy/acetylene torch around. I’m sure the homeland security wouldn’t mind at all.
Plus, if my smartphone were to explode in an airport[…]
Given the amount of energy stored in them nowadays, it ought to be possible to have a “blow me” circuit. That’d be the sort of thing one would expect from Tesla (“It’s just a minor software mod!”) – dump the whole battery charge through the memory all at once and let the molten stuff go where it will!
If we assume manufacturers have successfully been pressured into incorporating backdoors into their devices, wouldn’t it be much easier to access smartphones wirelessly?
You mean like the Intel Management Engine?
http://www.techrepublic.com/article/is-the-intel-management-engine-a-backdoor/
Basically, yes. There was a demo I saw a few years ago at CanSecWest where a guy overran a buffer in a cell phone antenna controller, took over its processor, and spawned a process on the main CPU of the phone over the bus (“hey, it’s all just memory at that point!”) It was impressive. I bet that guy’s making a good living doing that sort of code for you-know-who now.
That way mobile phones could still have all the security features that make it hard to crack, but also fold instantly (and quietly) if a transmitter nearby says, ‘Hi, I’m the government and I would like to search you.’ , in just the right tone of voice.
They’d be sneaky about it – it would be built into a ‘stingray’ so once it got the right phone ID it’d take it over, otherwise it’d leave it alone. That way they’d get a warrant for the phone and accidentally type the number (814-867-5309 as ***-***-****)
The intelligence community has a great history of subverting cryptosystems and management systems. There is no rational reason to assume they have suddenly stopped, after about a hundred years of doing it.
This is not to deal with three-letter agency subversion; this is to change the dialogue when officer porkface tells you to unlock your phone so you can delete the video you may of shot of him kicking that hippie’s ass.
I am so glad I don’t have a smartphone of any kind.
Caine@#3:
I am so glad I don’t have a smartphone of any kind.
Instead of making the tracking device attach around the ankle, they made it desirable.
Somehow I suspect if I brought in a dummy phone loaded with a dummy facebook and a dummy twitter filled with kitten pics they’d accuse me of being suspicious anyway and the whole rigamarole would be no different.
Shiv@#5:
Somehow I suspect if I brought in a dummy phone loaded with a dummy facebook and a dummy twitter filled with kitten pics they’d accuse me of being suspicious anyway and the whole rigamarole would be no different.
That’s a brilliant business opportunity, though!! Custom-populated burner phones and ipads for the discerning traveller: contains emails between you and cabinet members and congress people (including racist jokes) and budgetary information, sexy selfies from hollywood stars (carefully photoshopped) and carefully curated formerly-classified data.
I can’t recall if I’ve ever mentioned some of the stuff I carry in the encrypted volume of my laptop, for just those reasons. There are assembly diagrams for a Mark-82 H-bomb, specs for high speed bridge wire detonators and the Dash-1 for a Titan missile base. None of it is classified any more but… Uh, anyone want a copy?
@Marcus (#6):
If you’re offering, sure! Sounds like interesting read.
Sunday Afternoon@#7:
(and anyone else who may want it)
I’ve uploaded my humble little archive to google drive; it should be world accessible(see below)If you’re interested in someone’s archive, who has researched a ton of nuke weapon secrets, find a copy of Death’s Twilight Kingdom by Yogi Shan. I don’t know enough of the physics to tell how accurate it is, unfortunately. But it reads like Abdul Alhazred decided to write a book on nukes.
At the time it became part of my travelling file archive, Jose Padilla had just been sent to prison for having much much less research on making dirty bombs. So, at the time I thought, “ought to be safe to carry data about krytrons and ebw detonators because that’s all made of unobtanium, nobody’d take it seriously.” There I go, again, overestimating the intelligence of the establishment’s goons.
re #4:
Yes. And, of course, not just a tracking device, but one with a sensitive microphone and camera, all software-operated.
“iCloud is a great big wad of bits hanging out there, ripe for offline attacks, and there are techniques for embedding law enforcement access to keys into public key systems….”
Why else would so many tech companies be pushing so damned hard to get people to use their “free” cloud services? Because it removes every shred of privacy you have, and allows any police or government agency free access to anything and everything you post. It costs a huge sum of money to build, power, cool and maintain those servers, not to mention the huge expense for infrastructure. Apple, Microsoft and the rest are not doing this as a public service, after all.
Re: #2
Thermite is fun but not something I’d want to carry in my pocket (I’d prefer violent self-destruct mechanisms that are both stable and reliable). Years ago I took part in a little experiment, or, more accurately, messing-about in a lab where we tried different mixtures. We didn’t learn much, though, since one blinding fireball rising into the air looks much like any other blinding fireball. We nevertheless continued in good spirits until we ran out of crucibles.
The battery should be a much better way to dispose of the phone and its nosy thief. The way I see it Samsung has already made great strides, providing proof-of-concept with the Note 7 (or whichever the melty burny phone was). They just need to refine it a bit more.
Intel management engine:
The writer of the linked article seems very reserved and I certainly have no means of judging this issue for myself. I’d go with the author’s judgement because it seems sensible (but then most things can be made to sound sensible, especially if the audience has no clue).
But it’s nice to think of all the options I’d have if I decided not to trust Intel with my computer hardware. Let’s see, there’s … er … AMD*, who (maybe) by the end of the year can finally catch up with Intel. Oh, and the ARM-people, whose kit seems to be in every mobile device so that, if I wanted one of those, I’d be stuck with them anyway. What little I know of the techmarket seems to prove that capitalism does lead to competition giving the customer many choices. Colour me surprised.
*Fingers crossed that their rumored looming bankruptcy stopped them from investing heavily into backdoor development.
Maybe it’s just the jargon, but ‘take over’ sounds too aggressive for what I was thinking of. From your (very technical) example I gather the intrusion is at a very low level where the phone owner wouldn’t notice it unless they knew what they were looking for and/or had tools specifically looking for it.
So, to stick with the airport example, what you might end up is with an extra TSA-official sitting at the gate. And they’d have their own screen to look inside smartphones rather than luggage. I.e. go through files, pictures, apps installed. And of course the computer would also log everything it received from the phone. The passenger agreed to all this by booking a flight and entering the airport. More data for the retroscope, as you call it.
The cop might still decide to shoot both the phone and the owner because he feared for his life. After all, he might argue, his job is his life, and who wants to be suspended with pay for a few weeks (or whatever the current punishment is for uniformed murder)? I’d totally expect that logic to work in court. Lawyers, take note.
—
Former nuclear secrets are my second-most favourite kind of nuclear secrets. Thanks! (Before there are any offers: I’ll forgo my favourite kind until I have nation state to call my own.)
When I first got my smartphone, people asked why there is a piece of sticking plaster over the fingerprint sensor, inside the protective case. In recent months, people stopped asking and said, “That’s a good idea”.
It’s to the point where the only way to be sure your data is safe when travelling is encrypt it, put it on “the cloud”, and wipe everything on your devices. Then download the data and decryption software when you arrive.
I’d be interested to know whether there exists a good way to get through airport security that doesn’t mean you miss your flight but keeps data/photos/whatever that you may have in a device (laptop/tablet/phone) safe from the eyes of the goons? (Other than aforementioned encrypt/upload/travel/download/decrypt). Does any such strategy exist, or do you have to accept the risk that you’re not getting on a plane today?
@Marcus (#8):
Thanks for sharing, but I’m afraid that all but 2 files are not corrupted – the 2 files with valid sizes in the google drive listing.
Sunday Afternoon@#14:
Thanks for sharing, but I’m afraid that all but 2 files are not corrupted – the 2 files with valid sizes in the google drive listing.
Arrrgh, cloud computing!! I don’t know why I did that; I could easily have hosted it on my own site.
I used Google’s “drag and drop” interface and it said all the files were uploaded (and showed nifty checkboxes!)
There, and they all checksummed correctly. FTP for the win!
http://ranum.com/fun/old-nukes/
All present & correct! Many thanks!