Apparently we’re going to have to have regular discussions about email security, until politicians get their heads out of the sand and realize that they are targets and regular victims of mid-skill-level attack, and they need to level up their game if they don’t want to periodically look stupid.
Email security is not hard. I’d say “it just takes a little attention to detail…” but it doesn’t even take that much. I can only conclude that politicians are just blockheads about information technology and politics and it just shows how eminently qualified they are to lead high-tech civilizations. [stderr]
Politicians seem to think that the stuff they have to say is very important, which is weird, because if it’s very important, they ought to realize that what they don’t say is equally important. That, in a neat little frame, is the essential of communication security: control of disclosure of information in space and time. You’re not “on message” if your media machine is leaking data all over the place, whether it’s a result of internal factionalism, incompetence, or cyberspies.
Here’s a depressing scenario: right now, some marketing/PR weasel for some wannabe is cooking up the idea of a fake data breach/sextape leak/scandal that will “leak” out of email and get the wannabe’s name splashed all over the place – giving the wannabe a short window in which to capitalize on their notoriety and try to get their foot wedged in the door to fortune and fame.. Why not?
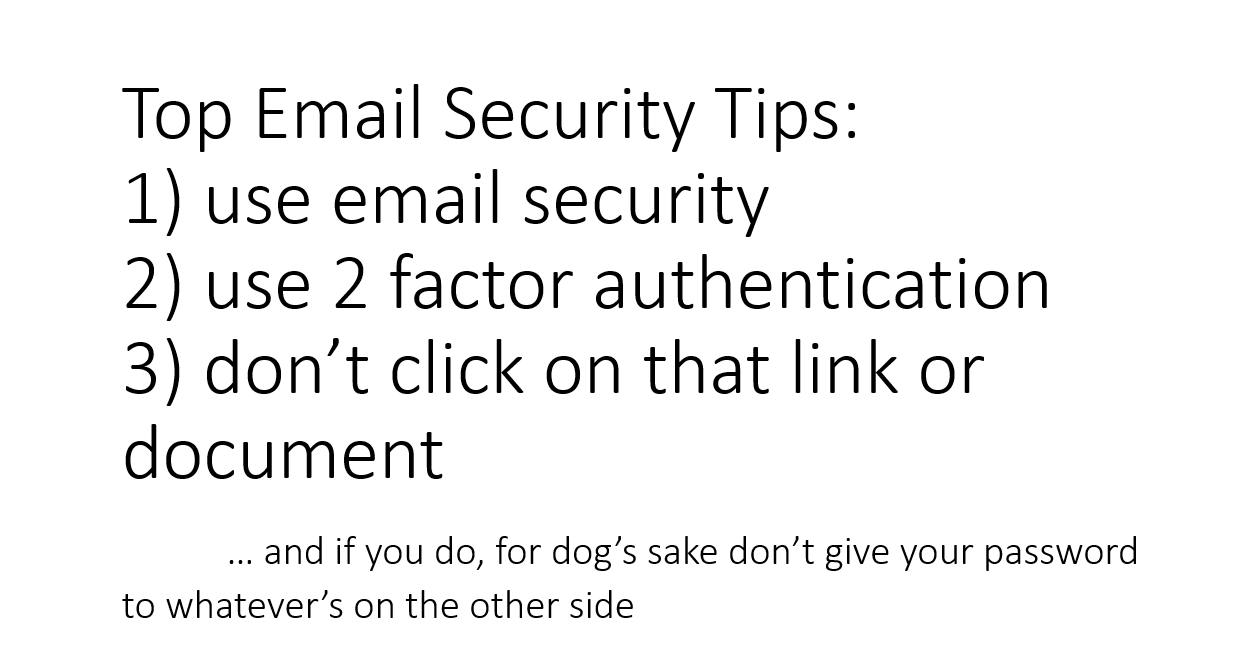
Figure 1
Macron’s campaign has done some interesting spin on this, attempting to divert us away from the basic point that their campaign is incompetent at IT.
As reported by The Daily Beast, part of the Macron campaign strategy against Fancy Bear was to sign on to the phishing pages and plant bogus information.
“You can flood these [phishing] addresses with multiple passwords and log-ins, true ones, false ones, so the people behind them use up a lot of time trying to figure them out,” Mounir Mahjoubi, the head of Macron’s digital team, told The Daily Beast for its earlier article on this subject. [beast]
 Oh, you say you do, or did. Why would you flood phishing addresses with multiple passwords and log-ins unless some imbécile in your organization had already given them a real log-in and password? This is akin to saying, “Oh, yeah, so you think you fooled me? Watch me put on a clown suit!” When someone sends you a phishing email, the only value you’d get out of dropping them a fake log-in would be if you had a professional security infrastructure in place and wanted to try to catch and back-track the attack when they attempted to login. But that would only work if you set up a honeypot by turning off your two-factor authentication. That’s like taking your helmet off in a jousting tournament so you can intimidate your enemy with how thick your skull is.
Oh, you say you do, or did. Why would you flood phishing addresses with multiple passwords and log-ins unless some imbécile in your organization had already given them a real log-in and password? This is akin to saying, “Oh, yeah, so you think you fooled me? Watch me put on a clown suit!” When someone sends you a phishing email, the only value you’d get out of dropping them a fake log-in would be if you had a professional security infrastructure in place and wanted to try to catch and back-track the attack when they attempted to login. But that would only work if you set up a honeypot by turning off your two-factor authentication. That’s like taking your helmet off in a jousting tournament so you can intimidate your enemy with how thick your skull is.
In the end, whoever made the dump may not have known what is real and what is false [beast]
It’s all real. Let me tell you what’s going on: the Macron campaign cleverly realized they could try to throw a head-fake that the emails were faked in case something turned up that was embarrassing, meanwhile they walked back the cat to see how bad it was. It’s a clever move: get your disinformation in line ahead of the other guy’s disinformation, now that you’ve been demonstrated to be stupid enough not to secure your email.
Here’s another reason it’s stupid: if you think that Brutal Bear, or whatever they’ve codenamed some random group of Russian IP addresses this month, is phishing you, then their tradecraft is better than yours and you’re not going to backtrack them and – even if you do – you’ll find that you can’t get your hands on them because they’re outside of your jurisdiction. Which is exactly how the last umpty-hundred of this sort of scenario played itself out. You’re not going to learn anything except you’ll get a well-deserved lecture from a security expert on how not to be a blockhead. I make my living giving those lectures, I know.
It’s also interesting the Hollande has vowed “a response” to the Macron hacks:
Mr Hollande told Agence France-Presse on a visit to a cultural centre in Paris: “We knew that there were these risks during the presidential campaign because it happened elsewhere. Nothing will go without a response.” [bbc]
Zut alors! That’s the combative attitude that La France is known for! Sacre bleu, c’est la drame!
Now, let me tell you the only effective response, and therefore the best, you can make to these attacks:

(for hints, see Figure 1)

PS – to any politicians: World-class security consultant available. Does not work cheap, will travel. Deeply experienced at secure system design, communications system design – including Email services and procedures, forensic analysis, and incident response.
One other point I’ve made before, that bears repeating: my accountant says there are only two kinds of people in hell: 1) those who were caught in the act and 2) those who kept notes. Or emails. These political email scandals don’t just show how blockheaded important politicos are about IT, it shows they have no tradecraft, or discretion, and are probably going to be horrible leaders because they can’t even think a few days ahead. Anyone running a campaign who doesn’t put some thought into communication security doctrine not just implementation, is setting up to lose a P.R. battle. Ask Hillary about that, what a clusterfuck her team created. It was so bad America voted in an even bigger bunch of incompetents.
I feel obligated to mention: given the US’ predilection for interfering with other countries’ democracy, and the incredible capabilities it has for doing so, it was probably the North Koreans that hacked Macron’s emails.
“Use email security” in Figure 1 is vague. But, basically, “turn on the capabilities you probably already have” is a good start. Don’t use google, use an SSL IMAP server hosted in the cloud (or better, a private data center) with 20-character random passwords, and make your users use a password vault (or if you’re providing them devices, pre-populate their email client with a password that even they don’t know and set it not to expire) Les foutus cannot have les mots de passe stolen if they do not savoir q’ils sont. Merde alors! Then the device you give them, with the pre-populated password: that’s their 2nd factor, let them unlock the device with a pin or thumbprint. It’s actually way easier security for the user than the foutu gâchis de Google.
Back in 1993, there was a meeting down at the Old Executive Office Building in DC, to discuss what to do for damage control in case Clinton’s email server whitehouse.gov was hacked after it went online. Since I was the guy who had set it up and locked it down, I was there, as was my boss Fred Avolio and Brian Boesch, our program manager from DARPA. “How do we handle the press?” was the question. I quite seriously suggested that we borrow a couple more SPARC 4MPs and have the Secret Service arrange a hush-hush briefing with some of the press: show them the row of SPARCs and tell them that they were all honeypots and the real system was locked down elsewhere. Once the press left, we could break all the machines down and put them to other uses. It would be a honeypot, all right – a honeypot for the media. Actually, the SPARC 4MP whitehouse.gov ran on lived next to my desk in Glenwood Maryland, not in Washington, which was a great bit of security design since the President’s emails went in to Washington FEDEX on floppy disk once a week. So if there was a security problem, we had already positioned it as not really a problem. Nobody liked my honeypot idea, but the 30-mile airgap turned out to be pretty darned effective.

It looks like if someone uses any system that still thinks that SMS alone is acceptable two-factor security, they don’t have security on that system.
https://motherboard.vice.com/en_us/article/we-were-warned-about-flaws-in-the-mobile-data-backbone-for-years-now-2fa-is-screwed
… politicians … are targets and regular victims of mid-skill-level attack…
Dear me. Who gets the high-skill-level-attacks, then?
Owlmirror@#1:
It depends what you call 2FA. It’s not necessarily SMS – I prefer a physical device that holds a copy of a key that the user doesn’t have.
There are flaws with anything, it’s all cost/benefit analysis, etc. My peers and I have had some success getting corporate execs to use that approach. Politicians collectively appear to be blockheads on this issue. I guess they don’t think they are important.
Pierce R. Butler@#2:
Nuke makers, people researching patentable molecules, microcoders writing device BIOS, systems administrators that run secure cloud services, encryption system developers, malware developers, intelligence officers, corporate executives that use better than basic security.
… Of course, any target that can be handled with basic stuff gets the basic stuff. Phishing appears to be all you need for a lotta people.
Given Hollande’s record, it might look something like this:
https://s-media-cache-ak0.pinimg.com/originals/18/95/59/189559d9b6856073cf872e3ae6b7559a.jpg
polishsalami@#5:
Ha!
As long as it doesn’t look like dropping a bunch of bombs on Raqqa.
If the French drop a bomb on Raqqa, it will certainly teach the Russians!
wereatheist@#7:
If the French drop a bomb on Raqqa, it will certainly teach the Russians!
Well, they bombed Raqqa because of a terrorist attack by French and Belgian citizens, it appears that bombing someplace is the preferred way of getting tough. When I want to show someone I’m annoyed about something, I fire cruise missiles. What do you do?
Would you care to elaborate on why not use Google email?
mafmaf@#9:
Would you care to elaborate on why not use Google email?
It’s a big target. There have been many successful attacks against elements of their architecture in the past including apparent state actors in the code-base. I assume it’s trapdoored to hell and gone. And of course the FBI has mandated ‘legal’ backdoors and dog knows what degree of cooperation NSA gets (signs point to high)
Another reason has nothing to do with security: it’s an ad platform. I’d rather pay a few bucks for a service where I don’t have some advertiser buying a distilled version of what I’m doing. That seems like a bad trade to me.
Addendum: since surveillance in the US is becoming political (always has been) it seems like an especially stupid idea for a politician to put their email in reach of the FBI. Do you think Comey’s above playing politics?