LastPass is, right now, “scrambling to fix another vulnerability” [ars] but I’m going to talk about it anyway. The unfortunate reality of how software is written nowadays is that it’s practically impossible to write reliable code – there are too many layers of abstraction and somewhere down in the bowels of something you embedded from someplace else, there are bugs.
I’m going to explain things a bit then I’ll drop into a nice easy workflow you can use to get this problem taken care of and have passwords off your plate, forever.
So, assume everything gets hacked a fair bit. Assume that your encryption is probably compromised, your operating system is compromised, too, and your internet connection is monitored. The first thing you want to do in any security analysis is figure out your threat model. Are you afraid of the NSA, or are you afraid of random bot herders and crypto-extortionists? The second question is: how many devices do you use passwords on, and do you care about having a synchronized cloud password service?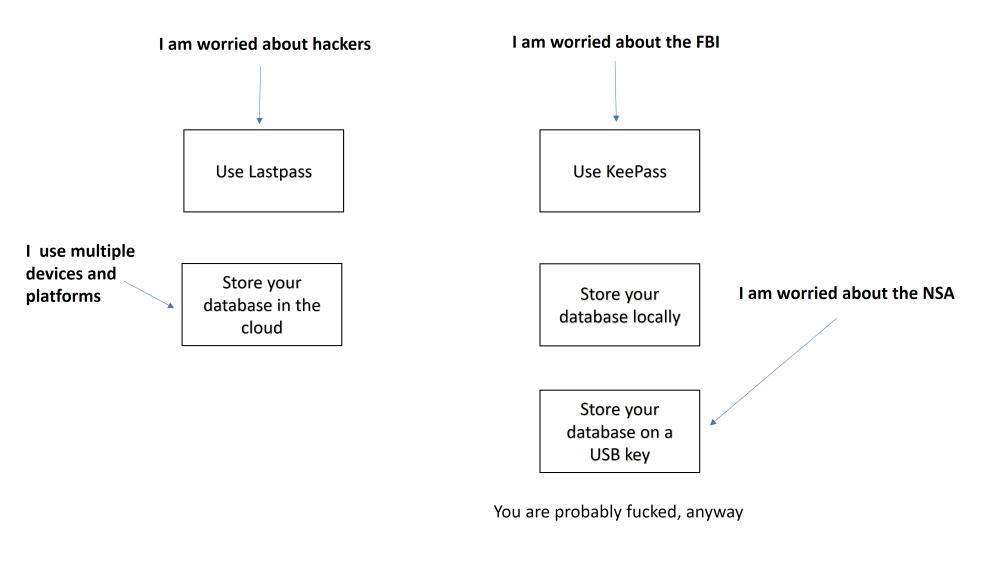 There are two really important things to understand, which most people don’t remember in time:
There are two really important things to understand, which most people don’t remember in time:
- The biggest danger with passwords is using the same password in multiple places
- If you forget your password you can almost always recover it
The best way of dealing with 1) above is to not ever actually know any of your passwords. That’s the big secret benefit of using a password vault: you never know your password, so you’ve got zero chance of reusing it and if you’re not reusing it that prevents one of your accounts being broken from leading to all of your accounts being broken.
Remember our assumption going into this: “everything gets hacked a fair bit” – if you’re using the same password on 10 websites, your password is as strong as the weakest of those websites. It doesn’t matter how long or complicated or hard to guess it is – if someone compromises the passwords on one website, they can do an offline attack against the hashes and then everyone who shares passwords between sites is screwed.
Your model should be that you’re only going to know one password and it’s going to be a phrase that’s darned hard to guess. I used to use: “Ce-ci n’est pas une password” (I deliberately made the French wrong, too!) that’s quite easy to remember; sure it’s a pain to type, but so is “18fja0-3kla8ke” or whatever some site’s security policy insists on.
Since a big piece of our threat is that we may re-use a password, we’re eliminating that threat when we don’t know them at all: it’s just as much effort to use a site-specific password as using the same password, and it’s actually easier to use site-specific passwords while you’re setting up your password vault. Your security will improve dramatically just by doing this. The one thing you don’t want to do is have a password for your master vault that is too awkward to scream at the CIA interrogators while they are waterboarding you. Corollary: do not use passphrases like “Allahu Akbar! I wi11 die before I tell you anything, crusader dog!” (Note the use of ’11’ instead of ‘ll’)
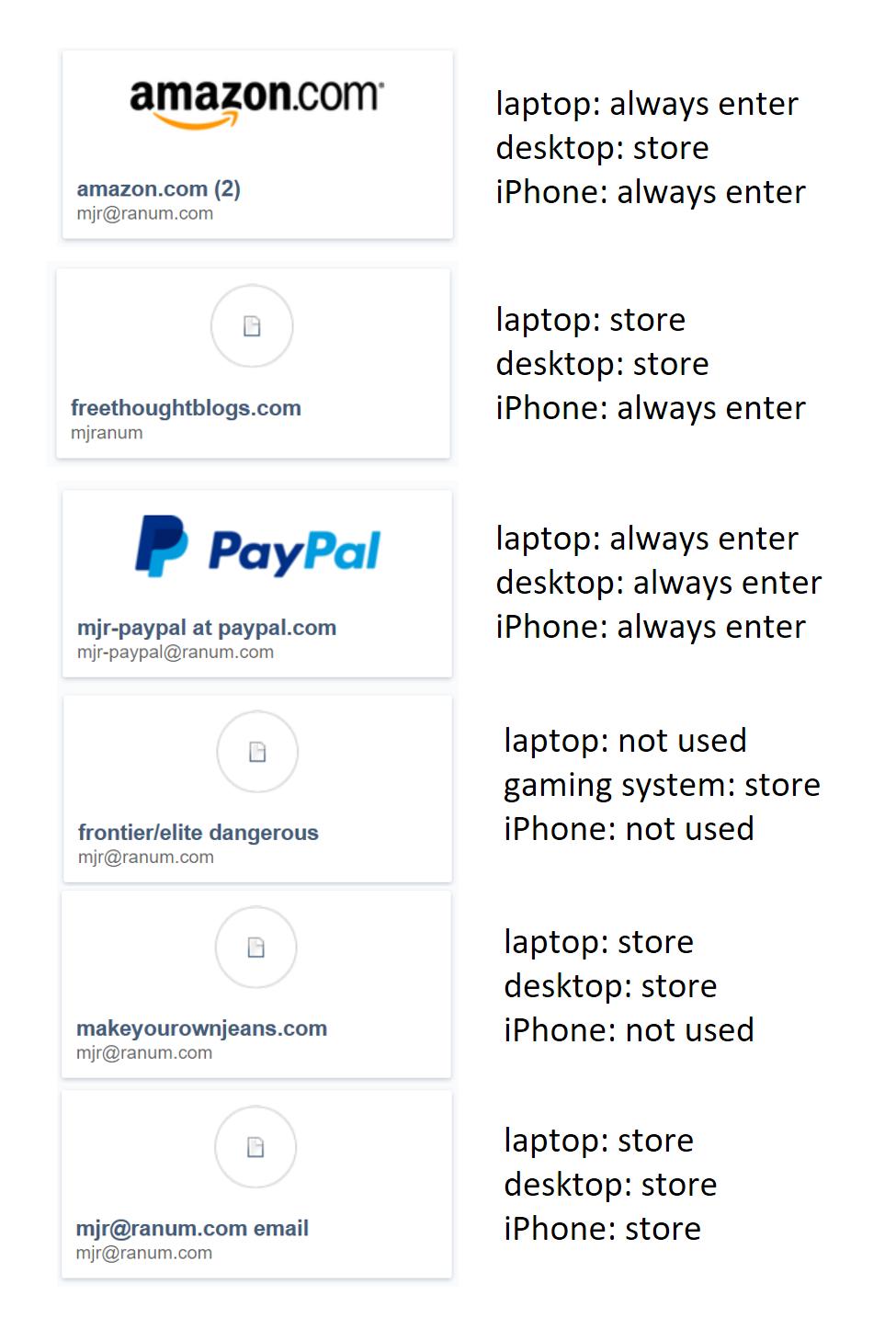 Another nice side-effect of using site-specific long passwords that you don’t know: it’s a bit harder to get tricked into giving them up. When you’re using site-specific passwords, it is OK to let your browser remember the password for a site, or to tell the site ‘remember me, I’ll be back” because your policy decision only affects that one site and you can enforce your own password changing policy. If you hear a particular site has been compromised, by all means, go change the password for that site. The important thing to remember is: you don’t even know the passwords for your own sites. Just to give you an idea how I do it, there’s a cognitive map on the left: it turns out there are some places where I hardly ever use certain passwords, anyway – it’s completely reasonable not to expose them everywhere.
Another nice side-effect of using site-specific long passwords that you don’t know: it’s a bit harder to get tricked into giving them up. When you’re using site-specific passwords, it is OK to let your browser remember the password for a site, or to tell the site ‘remember me, I’ll be back” because your policy decision only affects that one site and you can enforce your own password changing policy. If you hear a particular site has been compromised, by all means, go change the password for that site. The important thing to remember is: you don’t even know the passwords for your own sites. Just to give you an idea how I do it, there’s a cognitive map on the left: it turns out there are some places where I hardly ever use certain passwords, anyway – it’s completely reasonable not to expose them everywhere.
I do like having all my passwords in a network-reachable vault, because it has happened that I need to make changes on some site, and borrow a keyboard at a friends’ machine for a few minutes – in which case I have to open the vault on my iPhone, type in a bunch of spew, promptly forget it, and hope that my “friend” hasn’t got a keylogger installed. Even if they do, though, I’ve only exposed one password and if it were something important like my paypal password, I could just use the password vault’s password-changing feature (if it has one)
If you use this approach, you’ll find that you probably have 3 or 4 passwords that you’ll want to change every 2-3 months, but otherwise the rest of them don’t matter and you can store them in the browser or “leave me logged in” where appropriate. You’ll find that if you think in terms of managing passwords as stored credentials, you’ll spend less time worrying about passwords.
Now, how do you get started?
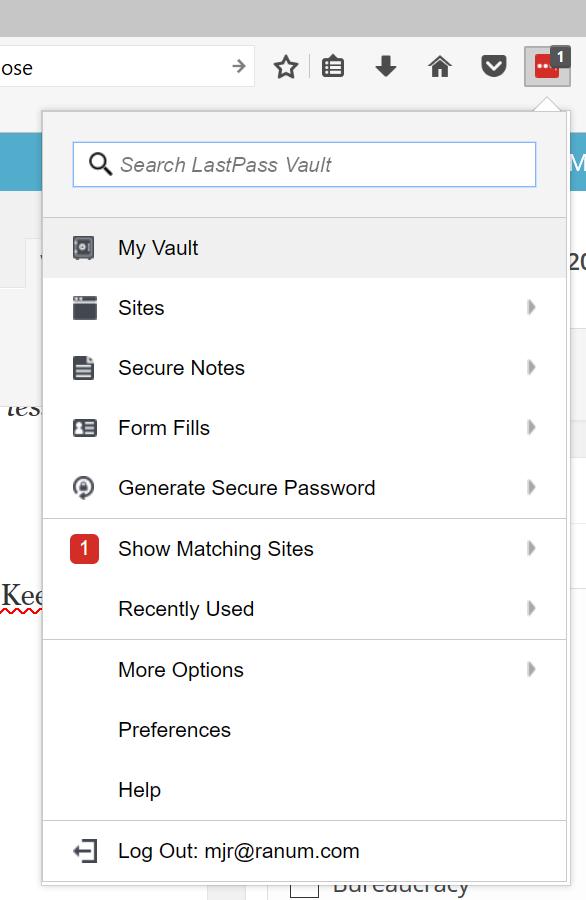
If you’re using a browser that has plugins (good idea) I suggest you install LastPass and the LastPass plugin. Or use KeePass and just copy your password vault around as/where you need it.
When the plugin is installed you can decide whether to have it always ask for your master password, or not, and you’ve got a few useful tools such as the “generate a secure password” option. The primary one you’ll use is the “Show Matching Sites” which you’ll notice is highlit with a red ‘1’ because it is matching freethoughtblogs.com/stderr right now.
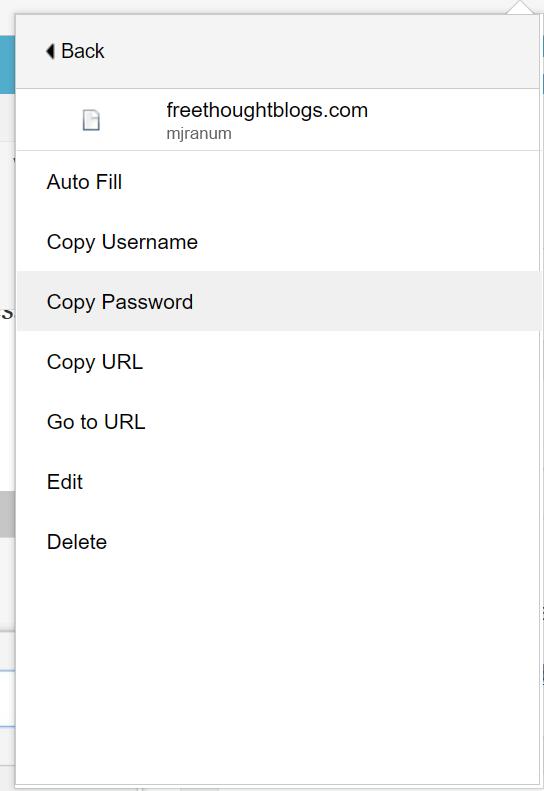 If I right-click on the “Show Matching Sites” it’ll give me a handy menu that lets me fill or display form fields, or edit the settings for that site.
If I right-click on the “Show Matching Sites” it’ll give me a handy menu that lets me fill or display form fields, or edit the settings for that site.
The simplest form of usage is to just “Copy Password” then enter my username, tab to the password field, hit paste, and I’m logged in.
If you configure the entries for a site correctly, with the login URL and username all filled out, when you go to the login page, Lastpass will automatically fill the fields for you: all you have to do is click the “Login” button and you’re in.
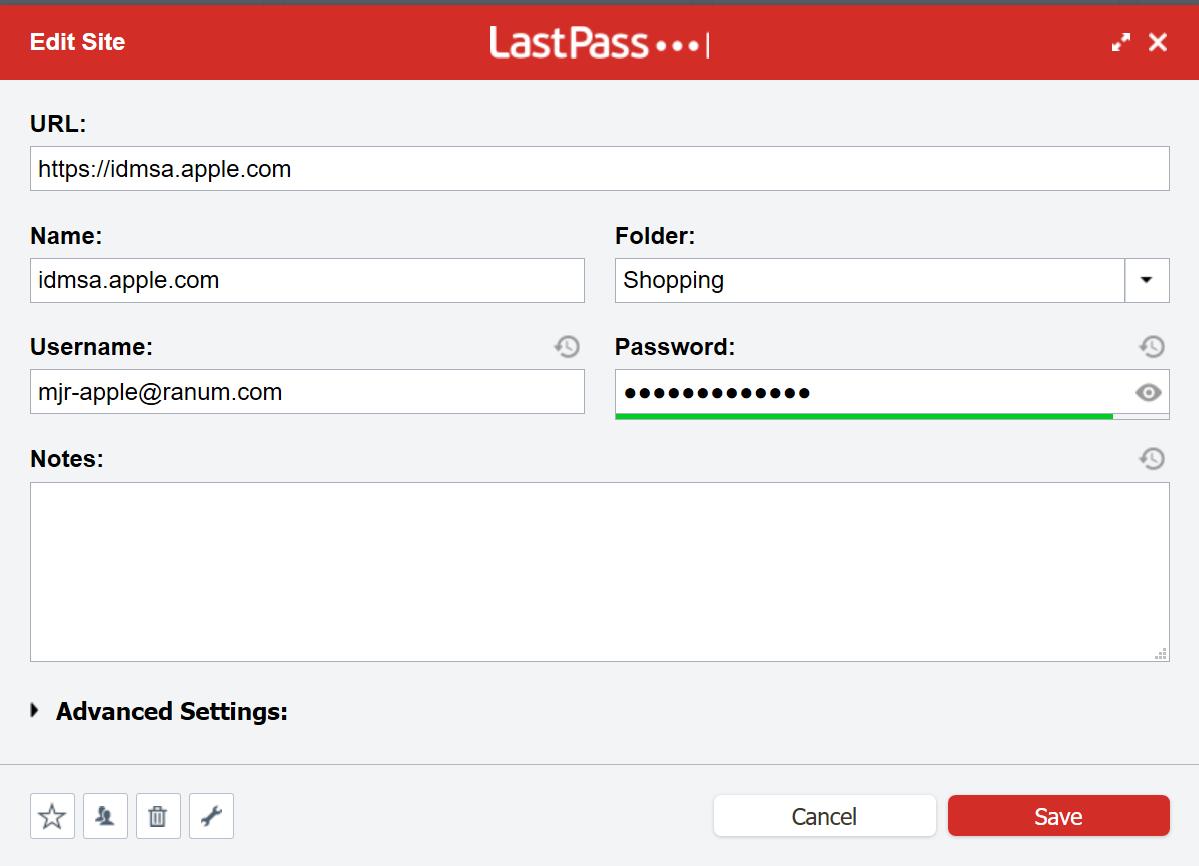
Once you have Lastpass or KeePass set up, then just go through the “I FORGOT MY PASSWORD” dance with every site that you know! Lastpass will ask if you want to save the site information, which automatically updates its database. I actually do it manually because I’m a weirdo. I’d demonstrate the process using my FreethoughtBlogs account except then I’d log out in the middle of writing a posting. Let’s fix my Apple Store account. I did that one a year or two ago and it’s relatively short.
You can see the URL and the username are filled in. I just go there:
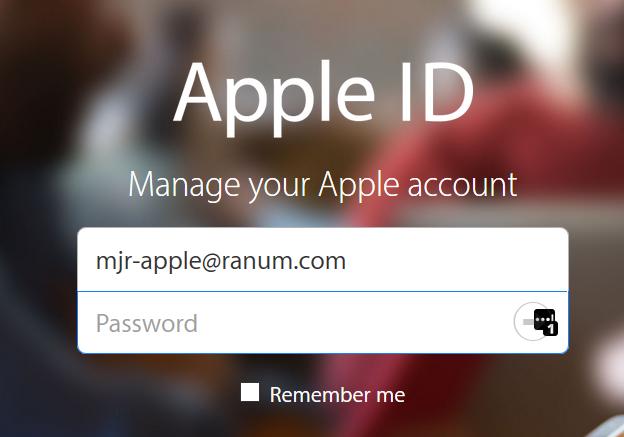
Then I copypasta my old password in, and drop into “change my password” – if I was super lazy I could just hit “forgot my password” and it would email me a message with a link to change my password. You’ll notice that the form field now has a lastpass logo and a ‘1’ – that’s it telling me that there’s one entry in the vault that matches this site.
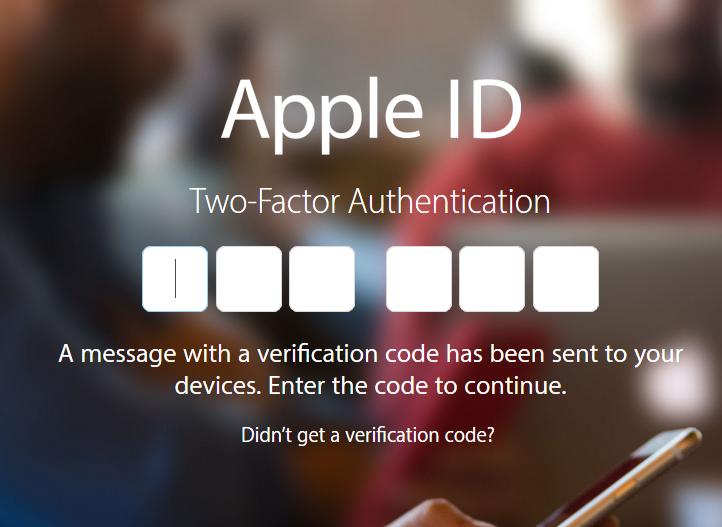
And let me mention two-factor authentication. You’ve already got your mental map of what passwords matter and which don’t. For any sites that you think “matter” turn on two factor authentication if you possibly can. Many people think two factor authentication is a huge pain in the neck: it’s not. It used to be. Back in the bad old days we security people would require two factor authentication for every operation, and that did suck. Now, when you enable two factor authentication on most sites, they only require the second factor for important things like policy updates, changes of stored credit cards, and password changes.
I CANNOT EMPHASIZE ENOUGH how important this is. When you read about various hollywood people, or political idiots, whose accounts are compromised and someone’s reading their email: they don’t have two factor authentication turned on. Imagine some Russian hacker was going to use my Apple ID to buy me a new iPad (yes! please!) and have it shipped to some loading dock somewhere. How did they get my password? Well, imagine I was stupid enough to use my Facebook password on my Apple ID. Now, they log in as me and – whups! My cell phone just got a text that someone was trying to log in as me. Most unsubtle. Yes, there are ways around two factor authentication, but none of us are worth anyone unleashing those sorts of techniques on us.
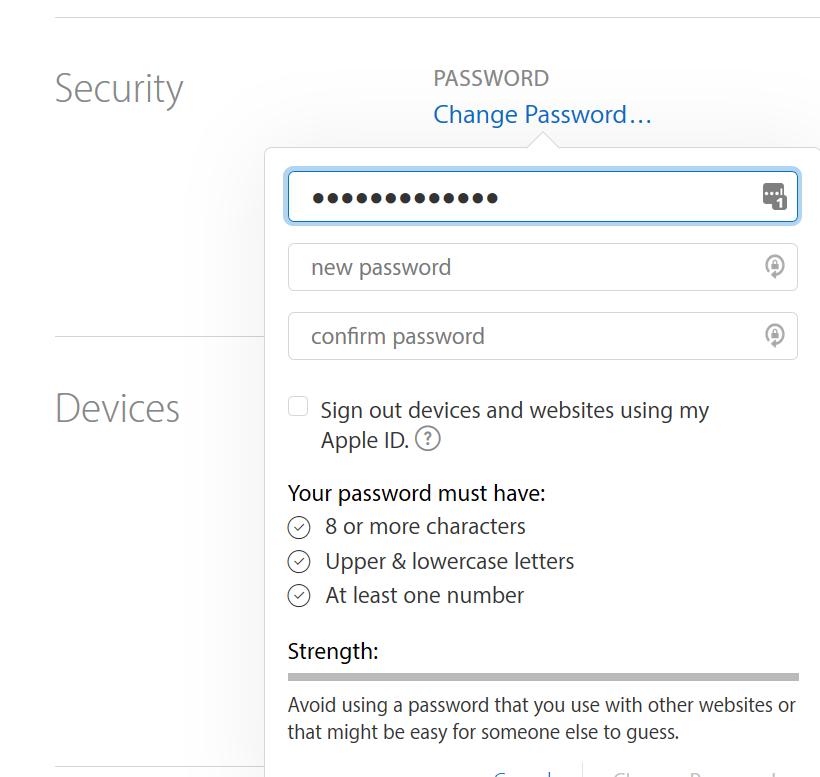
Now I am on Apple’s “change password” page and you can see LastPass is ready to fill in my existing password for me. You will notice that at no time in this process have I had to actually know my password.
You’ll also see a sort of lock and arrow symbol: that’s LastPass’ interface to its password generator – which, coincidentally, is exactly what we want to do.
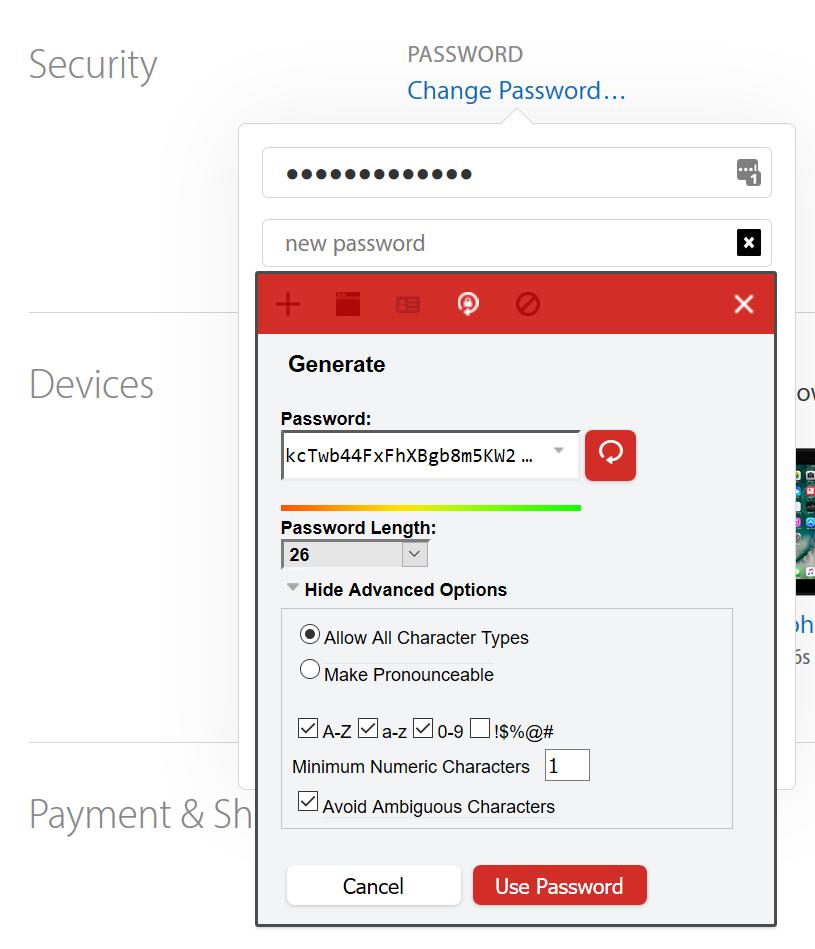 Click on the icon and you get the password generator page. It’s pretty self-explanatory.
Click on the icon and you get the password generator page. It’s pretty self-explanatory.
A pro tip, here: I like to avoid ambiguous characters. When you’ve just gotten off the plane from someplace and you’re logging into freethoughtblogs to post an entry from the airport in Stockholm, and your eyeballs are runny and your hands are shaking, it’s hard to tell ‘1’ from ‘l’ and ‘o’ from ‘0’ and when you’re using a 26-character password, you don’t have to! You don’t have to make it pronounceable, either: you’ll never have to handle it, normally.
Another trick I use: I keep a copy of notepad up when I am doing a bunch of password changes, and I copy/paste the generated passwords into notepad temporarily. Why? Some sites password change process appears to helpfully clear the copy buffer (there are attacks involving copy/paste) and if LastPass isn’t able to parse the password change operation correctly, it may not update with the new password and now it’s gone. In which case you have to do the “forgot my password” dance via Email. So I keep it in notepad in case, and check to make sure the change took.
By the way, no, that is not my new Apple ID password, there: I hit the generate button again after I did the screenshot. Nice try, though!
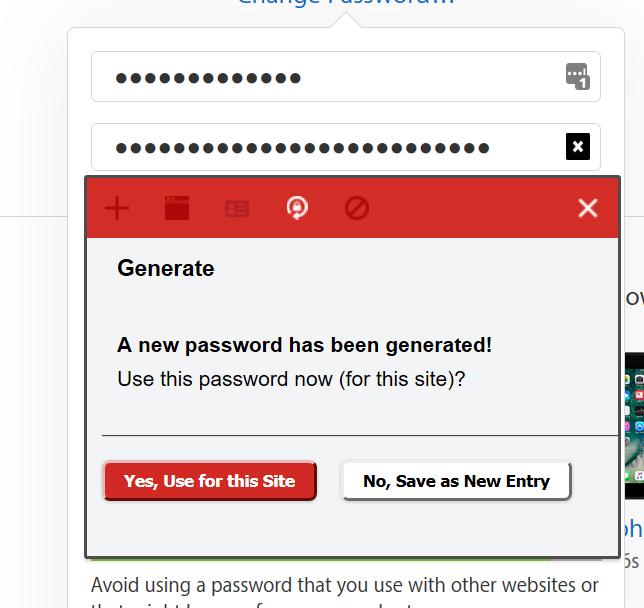
When you hit “Use Password” LastPass will stuff it into the form field and update its memory for that site. And you’re done. In the case of Apple ID I’ll have to enter the new password in my iPhone, iPad, and iTunes, and then I can forget about it for another year.
Another thing you may have noticed that I did: my Apple ID is [email protected], my PayPal is [email protected], and my Ebay is [email protected]. Why? A couple reasons. First off, if a hacker compromises one site, they’ll try the user-IDs on other sites. I see no reason to make that linkage easy for them; they’re mostly using robot scripts that aren’t very smart and when they don’t find an obvious match, they’ll go away. Also, by using different IDs I have a canary effect [stderr] – if I suddenly start getting email on my Apple ID email from anyone other than Apple, I know that something, somewhere, got sold to some marketing person.
When I tell LastPass to use the password, it updates the vault and that site is done.
If you want to bring all your passwords into a password vault, just do this process on every account you log into, until you’re down to a few sites that you’ve completely forgotten about. Whenever you run into one of those, do the “forgot my password” dance and assign it a new random password, then go back to forgetting about it again.
Most of us (be honest now!) use a single old password on a bunch of sites. I had two, that I used for almost a cringe-worthy decade. If you switch to using a password vault and large random passwords for the sites that matter, you can keep all those old ones which, by definition, don’t matter, and only change them if you ever log into them again. A good basic rule is: if it has your credit card information or naked pictures of anyone, then switch that account to using the vault.

If you have an IT department that insists on changing passwords every month, tell them I said they’re stupid. If appeal to authority doesn’t work, ask them to amend their policy to read: “passwords shorter than 24 characters must be changed every month. Passwords 24 characters or longer must be changed annually.” This will encourage people to use password vaults!
I should probably switch to KeePass but I’m lazy and password vaults historically are not great for importing/exporting to/from. The reason KeePass would work fine for me: I sync my iPhone and iPad using iTunes, so I could just sync the data down that way. And I sync my desktop and my laptop whenever I go on a trip, and my laptop’s home filesystem is an encrypted TrueCrypt volume. My vault would get automatically sync’d as long as I was careful not to stomp an update over top of another one, which is unlikely since I only use laptop (on the road) or desktop (home) at one time.
Back in 2013 or so, I was moderating a “panel of experts” with Alex Hutton, and John Stewart (yeah, three old white guys) speaking at MIS Institute in Orlando – with a room full of about 500 information security people – somehow we got onto the topic of “easy things to make security better.” Alex said, “Use a password vault and large random passwords!” and then I looked at him and we all three sang, in sort of harmony “use two factor authentication!” Then we stopped and I said, “show of hands: how many in the room use google.” Pretty much every hand went up. “Keep your hand up if you use Google’s excellent free two factor authentication” Only Alex, John, and I had our hands up. That was a really unsettling moment: a whole room full of security people were too lazy/inert/silly/goofy to use something as excellent as the two factor authentication that my friend Dug Song’s company, DuoSecurity, built for Google. Whenever you hear about “state sponsored attacks” where someone sends someone a phishing email and they give away their password, remember: 1) it wouldn’t have worked because the phishing site wouldn’t match the actual site in the password vault 2) two factor authentication would have still kicked in and you’d have gotten a txt warning you that you were under attack 3) you could not authorize the new device and the attacker would not get in. So, while I am sympathetic to people like John Podesta, whose accounts are compromised because their security is foolishly bad, I’m not highly sympathetic.
 If you want to get really paranoid, you can build one of these: it’s a hardware password vault that emulates a keyboard. You plug it in, hit a button, and it injects the password as if it were typed into a keyboard. It’s sort of missing a point, though, which is that USB devices that take over and become a keyboard: that’s what they keylogger the FBI installed is doing. The whole idea of plugging things in and out of your USB port is how you get malware like Stuxnet. So, while I like the concept, I like the strategy only somewhat. What I really want is tamper-proof operating systems running on high integrity hardware. But that’s not going to happen: the NSA will make sure they compromise any such system before it gets out in the wild.
If you want to get really paranoid, you can build one of these: it’s a hardware password vault that emulates a keyboard. You plug it in, hit a button, and it injects the password as if it were typed into a keyboard. It’s sort of missing a point, though, which is that USB devices that take over and become a keyboard: that’s what they keylogger the FBI installed is doing. The whole idea of plugging things in and out of your USB port is how you get malware like Stuxnet. So, while I like the concept, I like the strategy only somewhat. What I really want is tamper-proof operating systems running on high integrity hardware. But that’s not going to happen: the NSA will make sure they compromise any such system before it gets out in the wild.
Ways around two factor authentication: involve a man in the middle attack on your SMS stream and there are relatively few people who care enough to do that. All of their initials are 3 letters.
It used to be that you could “clone” a device by restoring a new phone as though it were a replacement for a dead phone. That was how some of the Hollywood personal pictures attacks were implemented: Scarlett Johansson’s Apple ID wasn’t very good and the attacker was able to guess it using information gleaned elsewhere (i.e.: she appears to have used the same password in multiple systems) then restored all her settings and cloud data onto a wiped phone. Apple has since added layers of “nope” around that sort of attack but – think carefully – it still means that there is probably an offline attack that the FBI can perform against your iCloud data. General hint: backup/restore is almost always a ripe hunting ground for offline attacks.

I don’t have a problem remembering passwords, but in the event I do, they are written down in a little black book.
Caine@#1:
That’s the old school way of doing it! One good thing about the black book is it’s got no WiFi, USB, or ethernet interface.
If you can turn on two factor on any important accounts you have, I still suggest it.
Do you have any shareable thoughts on cobsweb’s advice on Protecting Online Info?
Pierce R. Butler@#3:
I think the ship has sailed with regards to most of the basic stuff (like that) that you can do to protect yourself.
For example: providers clearly do not give a shit, and that is evidenced by the way they have worked around privacy controls whenever possible. Calling them and asking them nicely is not going to do anything; at best it means they may mask your name. As you can see here: that doesn’t work. No mechanism that assumes goodwill on the part of a vendor or government is worth its weight in unicorn farts.
VPNS, https everywhere, etc – those are all techniques that things like Verizon and google toolbar are deliberately crafted to get around. When that doesn’t work, you can be sure the provider either gets NSA TAO attention, or a national security letter if they are in the US.
I haven’t had a little black book in years! I currently use Norton’s password safe. I can only imagine what your thoughts are about Norton.
Marcus Ranum @ # 4 – That’s what I was afraid you’d say (except for the inexplicably missing “using TOR paints a bullseye on your ass!” minisermon).
Btw, something seems a bit agley on this post: only two of the graphics show up, and the rest just appear as little text boxes (“lastpass5”, “divider”, etc) – even after I told NoScript to “allow all this page” (twice, after which I no longer see its yellow banner) and refreshed the window. Even the tacky little clickbaity celebrity-toenail-fungus ads which otherwise always flaunt themselves after I do that haven’t returned.
Does NoScript do as little in blocking Google-snoopery as I fear it does?
Raucous Indignation@#5:
The Norton stuff isn’t bad. I think the key point about password vaults is that they’re better than any memorable password, by a long shot. I’m sure Caine’s memory is crazy great but I have something like 40 24+ character-long passwords that I don’t even know, so they can’t be stolen from me without a waterboard.
Pierce R. Butler@#6:
“using TOR paints a bullseye on your ass!”
… and it shines a searchlight on that bullseye.
Pierce R. Butler@#6:
Does NoScript do as little in blocking Google-snoopery as I fear it does?
I only use adblockers and NoScript to save bandwidth. There are a great many sites that flat out won’t work without google or facebook or whatever’s tracking links. We are all Melians on this web.
I don’t know about the pictures. Is anyone else experiencing problems?
(I assume they are in my browser cache from when I was writing the posting)
I’ve tried two password vaults (one from Intel, and I’ve forgotten the other one) and found they both didn’t log in to a lot of the sites I regularly use properly, so I had to type the password in manually instead of having it filled in by the browser when I typed the first letter of the id
I had to keep typing the password for the password vault when it logged out just about every day.
If I’m typing in usernames and passwords, even if it’s one password, doesn’t that defeat the purpose of the password vault?
How do you and Caine get around having your passwords on another device (or black book) and not type it in?
I find typing the first letter of an id and then the browser do the rest means I rarely type in passwords or ids, and it’s quicker than a clunky password vault that can’t log in to many sites, and I use two factor authentication when I can.
Brian English@#11:
If I’m typing in usernames and passwords, even if it’s one password, doesn’t that defeat the purpose of the password vault?
No! The purpose of the password vault is to allow you to have unique passwords for every site, and to not have to have memorable passwords.
Not having to use passwords at all, and relying on pre-exchanged certificates, that’d be a feature/requirement of a “web that does not suck” which is something we will never have.
Marcus,
This post was very timely for me. I had a conversation with our university security guy just yesterday and he recommended LastPass. I had not heard about it before and this gives me a sense of what that was is all about.
Thanks!
I’m still trying to get my head around securing the entirety of your data by introducing a single point of failure.
Brian @ 11:
I do type mine in. I don’t trust any software, especially browser built-ins, to keep or manage my log-ins. I keep everything on an extremely tight leash, at least as much as possible these days. As noted, half the ‘net won’t work if you don’t allow google tentacles all over.
On a much earlier post of Marcus’s, I noted that the first thing I kill off on any new device is any sort of update. I don’t let *anything* update automatically.
Azykroth@#14:
I’m still trying to get my head around securing the entirety of your data by introducing a single point of failure.
It’s security 101 stuff: integrity, reliability, and confidentiality are a triangle of tradeoffs. If you want to do away with single points of failure, you have to replicate things and build in recovery paths. Those recovery paths are going to be bad news if you want to keep your data confidential.
That said, I know I went on a bit, but I did point out repeatedly that you can use “lost my password” recovery if you lose your password to your vault. So, maybe you don’t need to get your head around any of this – it’s not really a problem.
It’s not just the losing, it’s the fact that anyone who can get your vault password can access everything with no additional effort.
Have you seen Jeff Atwood’s Password Rules Are Bullshit? It’s got some great recommendations for passwords.
Personally I bought a Yubikey recently and setup my accounts and apps that support it with it. It’s not perfect but is more convenient than using 2FA on my phone. You can even setup Keepass to use the Yubikey as the 2FA key but I havn’t tried that yet…
@ Azkyroth #17:
Fortunately it isn’t quite as simple as you fear. There would still be the 2 factor authentication to get around – I’ve just verified Dashlane (similar to LastPass) and they use Google’s Authenticator app to provide the second factor when attempting to log into the read-only in-browser view from their website. So even if someone were able to guess my password, they would have to have my phone, plus defeated the passkey or been able to persuade me to unlock the phone with my thumb.
I’ve been using Dashlane for going on 16 months and wonder what took me so long! Same as Marcus, I had an embarrassingly small set of passwords that I used on websites. Dashlane has a handy dashboard which analyzes your password library and recommends removing duplicates.
As a part-time web developer, I find Dashlane invaluable to manage my various levels of test users on my site, both live and development (sync’d across several caption & desktops). The integration with mobile safari on my iPhone is a huge bonus as my web app tries to be mobile friendly.
Oops – “sync’d across several laptops & desktops”.
@Pierce R. Butler
I’ve been having the same problem across freethoughtblogs (using Firefox+NoScript). I haven’t figured out what the reason is.
Workaround: put your mouse cursor over the text that corresponds to the image, right-click, and choose “Reload Image”.
Also, preview no longer works. Feh.
Aha. I think I may have figured out part of the problem.
I also have HTTPS Everywhere installed. I have, now that I think about it, seen problems elsewhere when some stuff was just not working properly via https.
When I disable https for Freethoughtblogs, and refresh using http, I see all of the images, and preview works again.
But why are there two images that do load when I use https?
Looking at the underlying HTML, I note that those images are the only ones whose img tag does not include the “srcset” and “sizes” attributes. I have no idea why that makes a difference.
Yes, using a password vault does mean you have a single point of failure – but it’s easier to protect a single point of failure than many points of failure. If somebody roots my machine, steals my database (I use KeePass), and installs a key logger to get my master pass phrase, then yes, I’m hosed – but I’m pretty hosed in that scenario anyway. I have over a hundred passwords to keep track of, so either I use a vault or I reuse passwords. If you’re reusing passwords, you have a small number of points of failure (each password, if you use more than one), but exposed in many different locations, all of which are out of your control.
Dunc@#4:
There are always single points of failure. It’s always seemed like a pointless quibble to me but it seems to be important to some peoplr. (Guess what: you could die – that’s another single point failure)
Putting all your eggs in one basket lets you watch that basket, and handle it carefully. They are still in one basket but that’s the point of the exercise.
Owlmirror@#23:
I dunno why it is doing that. I usually set the sizes on images to match some imagined flow. Maybe not setting them is screwing something up or making them look like banner ads?
Owlmirror @ #22: When I disable https for Freethoughtblogs, and refresh using http, I see all of the images, and preview works again.
Good catch! My problem started right after installing HTTPS Everywhere…
Howsomeverwise, the HTTPS Everywhere FAQ simply advises
– but actually doing so for the “Freethought Blogs.com” listing on the displayed menu (of the 13 items shown) only rotates the accompanying flag from a dark-green checkmark to a light-green checkmark to a red X – and the graphics (except the LastPass & Apple ID screencaps, which worked all along) on this page remain just labels in each case.
The FAQ also says:
– so I just did that via the “Tech Issues” button.
Correction @ my # 27: Now the rest of the graphics appear.
Possibly going elsewhere and returning forced a more complete refresh than the redraw which occurred each time I switched an HTTPS-E setting?
Hm.
I started using Chromium (which also has HTTPS Everywhere), and saw something similar to what I was seeing in Firefox: most of the images not loading. There was a shield with a red x, and clicking on it showed the message “This page is trying to load scripts from unauthenticated sources”, with the option to “Load unsafe scripts”. Clicking on the latter loaded the page with all images, but now the https: in the URL bar is red with a red diagonal overstrike and is preceded by a red triangle with an exclamation mark. Clicking on that shows “Your connection to this site is not private because the site loaded an insecure script.”, with an option to click on “Details”. Clicking on that brings up the inspector for Security, which says the the certificate is OK and the Secure TLS connection is OK, but also has a red x that says “Active Mixed Content – You have recently allowed insecure content (such as scripts or iframes) to run on this site.”
I can also look at the error log, which as a bunch of warnings like this:
(index):636 Mixed Content: The page at 'https://proxy.freethought.online/stderr/2017/03/31/using-a-password-vault/' was loaded over HTTPS, but requested an insecure image 'https://proxy.freethought.online/stderr/wp-content/blogs.dir/91/files/2017/03/lastpass.jpg'. This content should also be served over HTTPS.(there is a similar warning line for each of the different images that were failing to load)
And there’s also these warnings/errors when I click preview:
(index):8 Mixed Content: The page at 'https://proxy.freethought.online/stderr/2017/03/31/using-a-password-vault/' was loaded over HTTPS, but requested an insecure XMLHttpRequest endpoint 'https://proxy.freethought.online/stderr/wp-admin/admin-ajax.php?action=ajax_comment_preview'. This content should also be served over HTTPS.
(index):1 XMLHttpRequest cannot load https://proxy.freethought.online/stderr/wp-admin/admin-ajax.php?action=ajax_comment_preview. No 'Access-Control-Allow-Origin' header is present on the requested resource. Origin 'null' is therefore not allowed access.
@Marcus: Can you change the code for the images so that it just reads
/stderr/wp-content/blogs.dir/91/files/2017/03/lastpass.jpg(and similar)? That is, strip out the part reading:
http://freethoughtblogs.comfor all of the images loaded by the post?
I think that will allow the images to be served by https when the page is loaded by https.
I’m less sure what to do about the comment preview problem.
The page source has a line that reads:
var AJAXCommentPreview = {"loading":"Loading\u2026","error":"Preview error","emptyString":"Click the \"Preview\" button to preview your comment here.","url":"http:\/\/freethoughtblogs.com\/stderr\/wp-admin\/admin-ajax.php?action=ajax_comment_preview"};
(Note http: rather than https:)
Which I am pretty sure is what is called by the ajax-comment-preview.js javascript.
It might be possible to change that in this one instance, but I suspect that that line, among others, is all automagically generated by WordPress.