I suspect that there is an optimal and a peak conspiracy size, beyond which it becomes nearly impossible to keep a secret.
That’s one of the reasons why I tend to disbelieve conspiracy theories that involve a lot of moving parts. I completely suck at math but if I recall how this is calculated, you take the probability that any individual will leak, and then the probability your secret remains secret is the combined probability that all the individuals don’t leak. The way I think of it (because I suck at math) is that you make a saving throw on your Leak Table every year and sooner or later you’re going to come up ’01’
That’s why, historically, intelligence was managed on a “need to know” basis: you compartment secrets so that only the smallest number of people that need it get access to the information, then you carefully decide who gets access. In the world of classical intelligence there is an awareness that there are people who hoard secrets – it seems to be a mental quirk of the secret-trader mind and it makes sense if you assume that “secrets -> power” therefore the more secrets you have the more powerful and important you are. The secret hoarders are dangerous characters – for the agency keeping the secrets, because the only way to show your power is to reveal something about the secrets that you know. These secret squirrellers start off with “I could tell you but then I’d have to kill you” and end up revealing secrets to others, “look what I have!”
The NSA appears to have had a secret hoarder [stderr] and now it sounds like the CIA’s turn. And WikiLeaks is dumping some of their code:
By the end of 2016, the CIA’s hacking division, which formally falls under the agency’s Center for Cyber Intelligence (CCI), had over 5000 registered users and had produced more than a thousand hacking systems, trojans, viruses, and other “weaponized” malware. Such is the scale of the CIA’s undertaking that by 2016, its hackers had utilized more code than that used to run Facebook. The CIA had created, in effect, its “own NSA” with even less accountability and without publicly answering the question as to whether such a massive budgetary spend on duplicating the capacities of a rival agency could be justified. [wikileaks]
The problem with having over 5000 users of a software secret is that it’s not going to stay secret very long. For one thing, software exists to get distributed to run in lots of places, and for another it’s inherently easy to share: it’s usually nicely packed up sitting on some file share calling out to be copied to a USB stick. Hardware can be serial numbered and tracked, distributed as a black box without the users needing to know how it works inside.
If one of those 5000 users is a secret squirreler and takes a copy home, then shows a friend how cool they are (and the friend copies it) … another problem is the hacker mindset. I’m not saying “all hackers are sociopaths” but there’s a strong common thread of not respecting people’s data and privacy in order to be a hacker in the first place – so the CIA’s hacker teams are, ironically, the people least qualified to be handling this stuff.
The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.
Of course! What self-respecting hacker wouldn’t take a copy of that stuff!? It’s the ultimate hacker-cred, having a USB stick taped to the bottom of a locker somewhere, full of top secret CIA spy tools. And eventually it gets shared around and winds up on WikiLeaks.
![Source WikiLeaks [here]](https://proxy.freethought.online/stderr/files/2017/03/cia.jpg)
Source WikiLeaks [here]
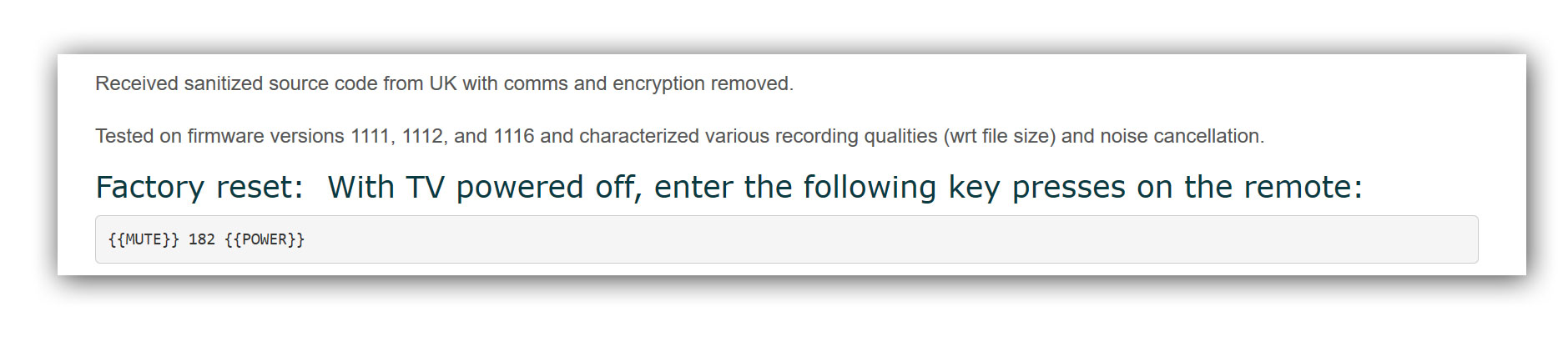
It’s going to take the security community a while to absorb this stuff. There are so many crunchy nuggets in it. “Received sanitized source code from UK with comms and encryption removed…” tells me there is an active ‘sharing economy’ between the 5000+ users at CIA and whoever else is in on it; they should have expected these secrets to leak. It’s part of the psychology of the police-state authoritarian that makes them the least attractive person to have in your minion-pool.
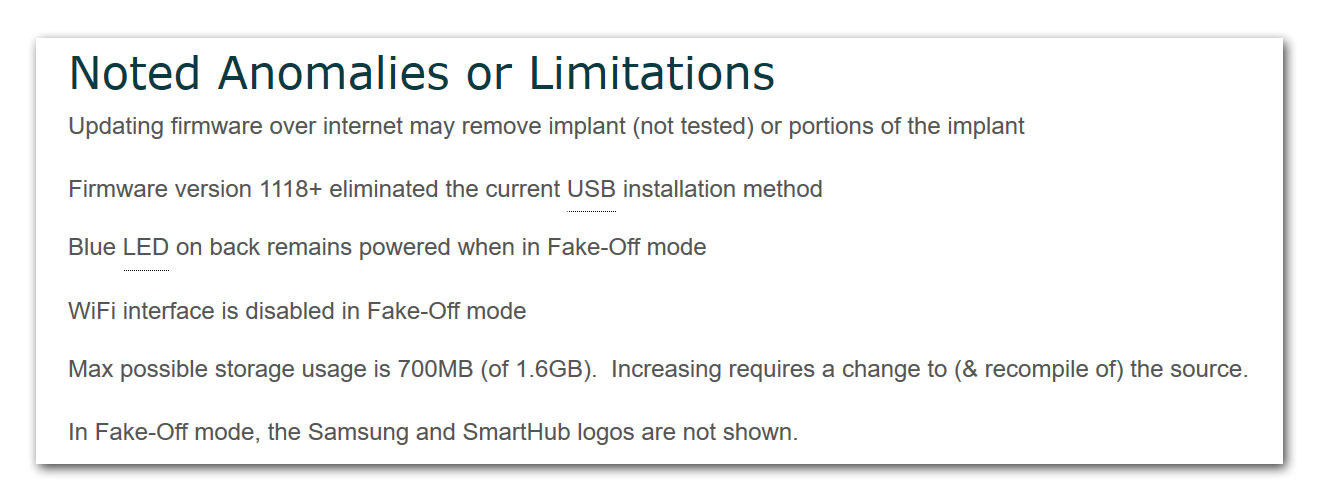
“Fake Off Mode” – it’s a thing.
The “characterized various recording qualities … noise cancellation..” bit: that’s talking about turning one of your Internet of Things into a surveillance device.

As I have said before: I am not entirely a fan of WikiLeaks. Sometimes, they give a black eye to our enemies. But that doesn’t mean they’re our friends.
I don’t think that secret-leaking is a simple probability – it’s going to have to do with the degree to which the secret is shared within the circle. So, suppose we have 5000 people with access to a secret codebase but 30 of them are actively responsible for quality assurance and testing: those 30 are going to have to copy stuff around and trade it around – they’re already copying it and trading it, the opportunity to lose a copy is much higher. You’ve also self-selected the people who are most likely to want a copy. “What could possibly go wrong?”

“Three can keep a secret if two are dead”.
(Allegedly by Ben Franklin, but oddly enough, not in his Wikiquote page — not even in the “falsely attributed section” — so, who knows?)
I read it somewhere BTI (before the internets).
Note about probability (i.e. how to make that calculation:
I have n people keeping the secret with the probability p (for each one) that he or she will leak the secret this year.
The probability that none leak in one year is (1-p)^n.
The probability that none leak in m years is (1-p)^(nm).
If there are multiple secrets – say k of them, then it’s (1-p)^(mnk) that any one secret will leak over m years.
It’s worth noting that most secrets have a half-life of importance. You don’t need to keep them secret forever. I don’t need to keep a meeting location secret past the time of the last meeting I expect to have there. I don’t need to keep (some) operational secrets after the operation is complete. Of course – some have a longer half-life, though rarely beyond the lifetime of the participants.
I found this here at phrases.org.uk.
@efogoto:
Thanks!
And I see now that the quote is here:
https://en.wikiquote.org/wiki/Poor_Richard%27s_Almanack
(using “may” rather than “can”)
Also interesting is the one that immediately follows it:
“Poverty wants some things, Luxury many things, Avarice all things.”