In an email, I am asked:
Assuming that the current administration is completely unaccountable to law, is it *technically* possible for them to data mine the electronic communications of their political opponents?
This is one of the reasons why privacy advocates have been worried about the growth of the intelligence state: unchecked “black” operations allow the centralization of power, placing the reins of the state in an increasingly small number of small hands. One of the first signs of a state flipping over to totalitarianism is when the power of the state is used to attack opposition parties – that’s a scorched-earth tactic intended to destroy all opposition and leave a single clique as the “last man standing.” When power is centralized enough that one person can step up and grab it, you have the transition from a republic to a dictatorship.
![Cashing in on notoriety [source]](https://proxy.freethought.online/stderr/files/2017/01/paula.jpg)
Cashing in on notoriety [source]
![Eliot Spitzer [source]](https://proxy.freethought.online/stderr/files/2017/01/spitz.jpeg)
Eliot Spitzer [source]
The Dennis Hastert case, in which Hastert “structured payments” of blackmail money to conceal a crime, is – for all intents and purposes – the same sort of situation as the Spitzer case. Where did the financial evidence for that come from? The only conclusion that we can reach is that, if you’re not clean, and you’ve covered something up in the past, it can be caused to come back and haunt you.
The vast apparatus of record-keeping and data collection does not exist to prevent future incidents, it exists to retro-scope the past
I am not trying to paint a conspiracy theory, but rather to illustrate that there is already a history of retroactive data analysis being used to take political figures off the game-board. Could the same techniques be used in the future? Of course they will. The question is whether they will be used even-handedly, to weed out official corruption wherever it may be found, or to weed out official corruption in the opposition party.
This is nothing new: the FBI investigated Martin Luther King’s sexual wanderings and recorded them, Nixon attempted to corrupt the CIA and IRS into investigating his political opponents, etc. We should expect this sort of thing from politicians – which is why computer security practitioners and privacy advocates have been waving warning flags over the intelligence community’s aggregation of power over domestic communications.
Back to the questions from the email:
The reason I ask is to know if I should be nagging our local organizers to encrypt their communications more.
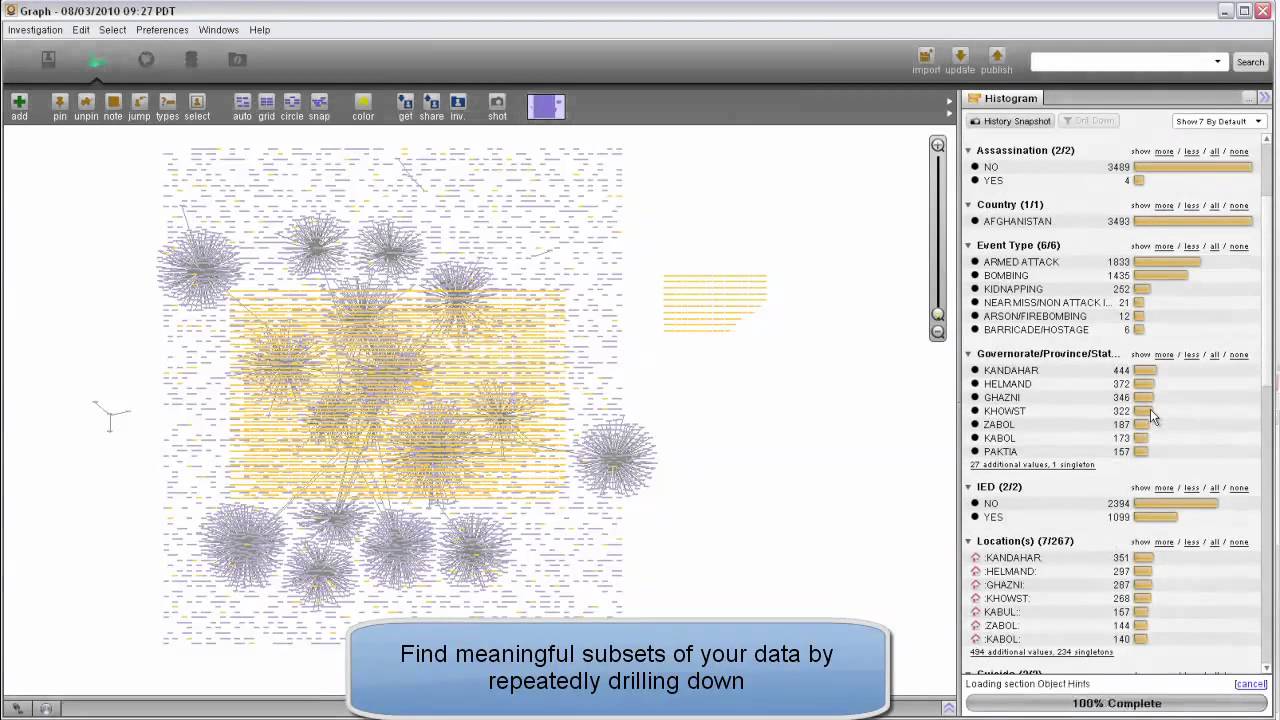
Palantir: cluster and visualize entity relationships and networks
It’s probably not worth even trying to protect your communications. They should assume that their communications have been compromised and that the very fact they are communicating at all means they will be subject to traffic analysis[1][2]. The US Government’s various intelligence agencies have been buying copies of Palantir like it’s going out of style. One should assume that if they regularly communicate with a group that is being investigated, they will be appearing as a pixel on a display like the one above. If you’ve been buying drugs on the “dark web” and you’re also a part of some dissident group, you’re going to be the pixels appearing as links between those two groups. When the establishment needs an agent-in-place in the dissident group, they’ll turn you, just like they did Sabu[3]: want to lose your kids? Your job? Spend some time in jail? No? Then we can work something out.

Ghost Dog sending SMS messages
If you want to communicate securely, don’t use the internet, or any national mail service, cell phone messaging, or … crap, what’s left? I’m reminded of Ghost Dog and his carrier pigeons as a way of getting messages to/from his feudal lord.
Either operate openly and understand the ground-rules of the world in which you communicate, or go off the grid. Those are your choices.
If you want to continue to operate in the grid, use Signal, or Protonmail, but assume that if you’re communicating using techniques intended to bypass monitoring that you’re going to be more closely monitored because you are doing so. In the old days it was accepted as a given that if you were using PgP your messages would be collected. Now it’s Signal and whatnot. The reason for this is important: they collect the messages and keep them, because if the communications channel is eventually compromised, then they can back-decrypt your traffic – it’s like a telescope into the past. Ask Petraeus and Spitzer how that works. Imagine if you’re using Signal for 5 years and in year 6 someone at NSA figures out a flaw in their random number generator that allows them to back-crack keys: those 5 years worth of stored crypto-blobs are now decrypted offline and fed into the analysis engine.
The email questions conclude:
The Indivisible Guide recommends using WhatsApp or Signal, but of course if you have better recommendations I am all ears.
I don’t, really. Assume your communications are compromised and operate as though everything you do is public.
I’m sorry it has gotten so bad. The cipherpunks[wikipedia] tried to warn everyone, starting back in the early nineties, but by then the battle-lines in the security community had already been drawn. There was a great deal of money to be made producing systems for surveillance and data collection on behalf of the police state, and many practitioners gravitated toward the money. Capitalism works that way: it forces you to forge your own chains, then punishes you if you complain later that they are uncomfortable.

By the way, if anyone wants them, the tutorial notes for my 1997 USENIX class “Secure Communications Over Open Networks” are here. Unfortunately, I never PDF’d the notes pages. It’s quite dated, now, but the problems are still the same. I describe the ssh-VPN-over-PPP trick, which was only known to a few ultra elite hackers in 1997, but which has since become reasonably well known. Also, the trick of using bulk encryption (in my example I used PGP) over backchannels like in-game chat has been publicized. There was a while when the FBI was seriously worried that ISIS was going to use World of Warcraft as a communications channel. As if! Anyone cool would use League of Legends. (Actually, they’d use steganography to carry superencrypted messages through one of the myriad image-sharing services, or paper letters delivered by hand)

Well, Marcus, I assume that you are like me and accept that you are on watch lists. In your case as a computer security professional. In my case as a now retired, Process development chemist and member of the Royal Society of Chemistry who has strong anarchist leanings.. As a result I do not worry about the way any posts I make or documents to be found on my computer would be interpreted-life is too short for paranoia.
I do know that no competent conspiracy would use the Internet but would revert to old fashioned trade craft, with one exception, where tactical security was adequate.( by that i mean, If I plan to rob a bank tomorrow and Email you the details, tactical security would mean the message takes until Saturday to decipher.)
AndrewD@#1:
I assume that you are like me and accept that you are on watch lists. In your case as a computer security professional
Yes. It’s interesting because some people I have, at various times, rubbed shoulders with have turned out to be troublesome to the establishment. I suspect I have a fairly low score in Xkeyscore, but I don’t know.
In my case as,as now retired, Process development chemist and member of the Royal Society of Chemistry who has strong anarchist leanings
Oh, my, yes. If you ever swapped email with anyone who ever swapped email with anyone who worked on explosive lenses for nuclear weapons, for example…
I do know that no competent conspiracy would use the Internet but would revert to old fashioned trade craft, with one exception, where tactical security was adequate.( by that i mean, If I plan to rob a bank tomorrow and Email you the details, tactical security would mean the message takes until Saturday to decipher.)
Agreed: tactical intelligence is a problem that the NSA’s approach doesn’t address. Which is why the FBI have been completely incompetent at dealing with ideological mass-shooters or the Boston Marathon bombers, etc.
If you’re not familiar with the maneuver Paul VanRiper pulled in Millenium Challenge 2000, it’s a hoot: assume your opponent is reading your SMS texts and chat inconsequentially on that channel, while having your real messages hand-couriered. Ha! That showed ’em!
Excellent post, thanks.
.
From this, it seems the main reason encryption might be worse than just going ‘naked’ is that it would attract attention.
.
It doesn’t sound as if one has much to lose though. The government already has an effectively infinite record of everything you’ve said with or without encryption, the only difference being that with encryption they may have to wait a long time, or forever, to read your data.
.
Also hypothetically, if everyone used encryption for even mundane activities, the signal-to-noise ratio will plummet for whoever is doing the snooping. Encryption-based video games? Encryption-based grocery store apps? Bots that do nothing but blabber encrypted nonsense to each other all day from all over the world?
.
But yeah, two cans and a string still beat this.
.
Any thoughts about ad-hoc mesh networks?
.
Rays of hope may be thin, but can we survive if we don’t find a way to fix this mess?
multitool@#3:
From this, it seems the main reason encryption might be worse than just going ‘naked’ is that it would attract attention.
I don’t think it makes much difference. The way systems like Xkeyscore work is they take a variety of attibutes and assign weightings to them, then propagate something as “interesting” if more than a baseline score of points is calculated. So, let’s say that your weightings look like:
+1 destination is in middle east
+1 destination is in russia
+2 message is encrypted
+3 message appears to be steganographically concealed
+5 message contains content matching “talking about killing someone” list
+2 message contains content matching “talking about selling heroin” list
+1 message contains content matching “hacking techniques” list
Then this posting would score about a 1, whereas a message from a US soldier in afghanistan talking to a friend via PGP about buying a block of heroin would score a 5. Then the system prioritizes the alerts, let’s say anything that scores 10 or more pops up on an analyst’s console.
These scoring systems get interesting when you add network effects:
+1 message is “2 hops” from a person of interest
+5 message is “1 hop” from a person of interest
+1 message is from a member of a group we are interested in
+4 message is from a person we currently have a case file on
-5 message is from someone we have flagged as confidential informant
+10 message is from someone who has never communicated with the person of interest before, but who is also flagged as a person of interest
+10 message is from someone who has, in the past, exchanged encrypted messages with person of interest but this message is unencrypted (known plaintexts!)
Now, thread the messages coming to/from a person of interest, and sort them by score.
This technique is something I did an open source implementation of, for network security analysis, and it worked great. 2009 paper is here. My implementation was extremely meta- abstract and can be used to build scoring systems out of anything that you can render as a string of text. When Binney started talking about thin thread, my co-author and I had a good laugh. Basically, we published a roadmap for how to build an open source Xkeyscore.
It doesn’t sound as if one has much to lose though. The government already has an effectively infinite record of everything you’ve said with or without encryption, the only difference being that with encryption they may have to wait a long time, or forever, to read your data.
I wish I were that confident in encryption. I believe that the situation there is vastly worse than it appears to be. I suspect that there are relatively few things that haven’t been back-cracked.
Also hypothetically, if everyone used encryption for even mundane activities, the signal-to-noise ratio will plummet for whoever is doing the snooping. Encryption-based video games? Encryption-based grocery store apps? Bots that do nothing but blabber encrypted nonsense to each other all day from all over the world?
So the problem then becomes that the person running Xkeyscore writes a blabber detection algorithm and weights “blabberer” at -30 and the blabber instantly vanishes from the consoles. Until someone tries to hide in the blabber and then the new scoring modifier is based on detecting the attempt to hide.
Any thoughts about ad-hoc mesh networks?
They’re a good idea.
Back in the day a friend and I got some enquiries from a rather unusual source asking if we would be willing to design technology to make it easier to build communicatons infrastructures to facilitate revolutions. And ad-hoc mesh networks seemed like a good way to do it (we were thinking about using a mesh network to carry flood-fill messages, like old style USENET news, with grouped encryption envelopes) The access points were going to be cigarette-sized devices that could run off a car battery (about 2 months per charge) or be alligator clipped onto the power leads of an unsuspecting cop car, bus, or taxicab and velcroed under the hood. Or simply hooked to a motorcycle battery, put in a ziploc bag, and tossed down a ventilator or storm drain. Then the system was going to vampire-tunnel its comms over available real internet portals if it found them. Uh. So we completed a rough design, looked at it, and then decided we were not going to let the people who were asking for it have anything remotely like it. And it wasn’t the Russians asking, either. It was a US entity in the private sector that was interested in helping destabilize countries the US wants destabilized. Paranoia much?
Of course, the CIA have a long history of using front companies…
Anyway, they have Twitter now.
Dunc@#5:
Anyway, they have Twitter now
Yep.
I believe the idea was to also open a media-closed country up to Decadent American Internet(tm) in the event that some country had the temerity to try to shut down Facebook and Twitter. By the way, I don’t for a minute think that Facebook’s goal of increasing broadband to everyplace is entirely innocent. They’re “voice of america 2.0”
Hi Marcus,
If the US is mostly offensive (apologies if I misunderstood you saying this), is it another country (cough, Russia, cough, China, cough) have gained access to the vast trove of data? And being smart types, haven’t tipped their hand?
I gave of status book years ago, and have a twitter account that I use about twice a year. But I’m sure my pathetic attempts to read Pravda, Tass, Die Welt, Le Monde and regular browsing of El Mundo, plus insane screeds in comments sections of English language media probably ranks me as super spy? Nope?
Brian English@#7:
is it another country (cough, Russia, cough, China, cough) have gained access to the vast trove of data?
Eventually it will happen if it hasn’t happened already.
I think the more likely scenario is that some foreign agent will get a job at some other federal agency and then have access to the NSA’s trove through there. It’s very nice of them to put it all in one place, isn’t it?
There are currently some ridiculous number of people with top secret clearances – something like 200,000+. That’s a hell of an attack surface.
I’m sure my pathetic attempts to read Pravda, Tass, Die Welt, Le Monde and regular browsing of El Mundo, plus insane screeds in comments sections of English language media probably ranks me as super spy? Nope?
You’d be higher ranked if you read Al Jazeera and maybe participate in a few of the FBI-sponsored jihadi websites.
Ahh, I’m such a loser I’m not even going to be on a most dangerous citizen poll!
Yeah, I’m surprised how poor the security seems to be.
I’ve previously had access to Oz Tax department servers. So, I guess if they let a tool like me access important servers, they’ll let anybody.
Have you looked at Guifi net ?
.
On the one hand I’m impressed that a mesh network can wrap around a country. On the other I have no idea how it works economically or if we could import it.
.
In DC we had a burst of enthusiasm for meshes around the Arab Spring, (e.g. Commotion Wireless and Byzantium.) Some meshes were set up, I don’t know if anything is left of them but all of the sources are still out there.
So out of curiosity, who exactly is running the surveillance state and to what end?
It’s obvious they don’t answer to the “official” government in any capacity since they actively worked against Obama’s appointed heir even while he was still president. I doubt anyone who is nominally “elected” has any power over them at all. So are they basically acting as a government unto themselves? Are they working for their own profit, or is this one of those things where they started with the best of intentions to protect lesser-evil America from greater-evil Soviet Union and over the years “America” morphed from an actual group of people with actual lives to benefit or harm into an abstraction similar to how fundamentalists view God or the Bible— kind of a blank morality check that lets you do whatever you want in the name of the idea of a goal long since forgotten?
@Jessie Harban. It’s either The Knights Templar, Illuminati, Rothschilds, Girl Guides, or Medicins Sans Frontier.
I think they call it the deep state. It’s organizations that continue on through inertia and self-preservation that end up existing and serving themselves (or the wants of those in power in those organizations, not those who nominally run the organziation).
aka “the Iron Law”
I wonder… If we use some kind of strong encryption, and then use microwave radio to send the message EME (Earth-Moon-Earth, using the moon as a reflector), would that remove the risk of network analysis? The weak points would be message security on either end, but the communications channel itself would be as secure as possible, or am I missing something obvious?
Such communication would be illegal, I am pretty sure, but again – how would they be able to identify you as the culprit?
Jessie Harban@#11:
So out of curiosity, who exactly is running the surveillance state and to what end?
It’s what I call an “emergent conspiracy” — a general trend toward centralization of power, by people who want to get closer to a power center and act in an unorganized manner, all pushing in the same direction. It’s a bunch of authoritarians who believe that a certain way is the easy way or perhaps even the best way and they act independently toward the same end.
Basically, it’s what happens when too many squirrel people get in control of too much: things start to get squirrelly.
Actual conspiracies don’t make sense at this scale. But if you imagine that there are plenty of mid level people at CIA who think it’d sure be a lot easier to get things done if they broke a few bones, and some people at NSA who think it’d get the job done better if they ignored those pesky constitutional issues – eventually when such people get closer to power, that’s what happens. They’re not working together, they’re all sneaking in the same direction. The problem is that when you have a situation where the status quo is inaction, you implicitly favor people who are willing to take action, unless there are specific guards in place to prevent it. And, because the people who are willing to act are acting against inertia, it favors their finding a clever path around that inertia – they’re not even being sneaky, they just think they are “interpreting the law so that they can get things done.”
felicis@#14:
I wonder… If we use some kind of strong encryption, and then use microwave radio to send the message EME (Earth-Moon-Earth, using the moon as a reflector), would that remove the risk of network analysis?
There are easier ways to defeat traffic/network analysis, but the problem is then that they compromise your endpoint technology (which TAO has already done)
The easiest way to do it is something like old USENET news carrying streams of fake messages and spam, with the ability to inject real messages into the stream. If everyone gets the stream (per your example of lunar broadcast) then it is hard to see who is sipping what message.
That’s basically the trick behind the old “numbers stations” on the radio. You could tune in and there was just the voice of someone reading a list of numbers, slowly and clearly. Since it was broadcast, nobody could tell who was tuning in to the stream at what time. Presumably the numbers were one time pad data.
I’ve heard those stations (and there is – or was, at least – similar using morse code).
The problem with a broadcast is you can locate one point (the sending station). With EME, you are limited to the knowledge that the sender and receiver are both on the same hemisphere facing the moon. I would be a little concerned about that transmitter being found – you would want a highly directional transmitter, but you could get some process gain with spread-spectrum to reduce the power…
With the USENET idea – wouldn’t there be some way to identify who inserted what traffic? (I know next to nothing about the protocol, though I read plenty of newsgroups back in college…)
I think the big problem is day-to-day communications. Our social networks are built on easy communication, and we cannot all use exotic means to talk to one another – that allows the mapping and compromise of a network, even if the communications are innocuous… Ugh- this is getting depressing.