Reports have appeared that the US ran a cyber war program infecting the networks that manage Iranian centrifuges with computer viruses intended to slow down the production of weapons grade fissile material by the pariah nation:
(New Scientist) — This revelation is at the heart of an apparently impeccably-sourced book due to be published in the US on 12 June. In Confront and Conceal: Obama’s Secret Wars and Surprising Use of American Power, author David Sanger alleges that Stuxnet, which eventually wrecked hundreds of uranium centrifuges in Iran in 2010, was created by cyberweapons experts at the US National Security Agency in collaboration with ‘Unit 8200’, a cyber operation of Israeli intelligence.
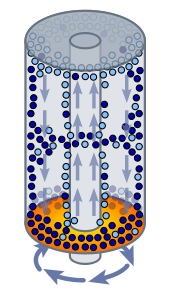
Centrifuges are devices that separate and purify the type of fissile material needed to produce a critical reaction, i.e., the heart of an atomic bomb. It’s called enrichment. Enrichment is necessary because the material, usually Uranium and Plutonium, come in different isotopes, atoms with the same number of protons but different numbers of neutrons, and some isotopes are better for weapons or reactors than others . The differential in weight between the isotopes is tiny, so one way they’re separated is by putting the raw stuff in the form of a gas/fluid compound in big cylinders standing on their ends like missiles and spinning the cylinder hundreds of times a minute for weeks.
The exact percentages of fissile material needed for military reactors or weapons is generally classified (And trust me, on the weapons side of it, what you see quoted on the Internet or what your uncle read in a book may or may not be anywhere near accurate). But conventional wisdom is low single digits, around 3 – 5%, are used in civilian land-based nuclear reactors, low double digits serve as reactor material in nuclear subs, and very high purities in excess of 90% are needed to produce a critical runaway atomic reaction like the one that devastated Hiroshima. It takes a number of those fission reactions all going off with perfect timing arranged in a precise geometry to squeeze and heat the very light elements in the core of an H-bomb. In short, to have a nuclear weapons program, you need a lot of weapons grade highly enriched fissile material. It’s a damn good thing for our planet that making a few kilos of this stuff takes a huge amount of time and work.
In the 1950s and 1960s the US developed really big centrifuges that could turn out large amounts of weapons grade material. That technology worked well, but the tolerances are unforgiving; it takes extreme manufacturing precision and constant attention to components to keep production rolling. Just the over-sized ball-bearings alone were a constant pain in the ass for the good ole boys at Oakridge. Other researchers developed another method, a simpler, more scalable approach using much smaller centrifuges. Instead of dozens of very large ones, they had a whole series of them, hundreds in a row. Centrifuge A would produce a particular purity and that material would be piped to fuge B and so on. You don’t get as much refined material as quickly, but the smaller machines are easier to build and maintain, if one has to be serviced it can be valved off and the material just goes to the next one in the series, and the host nation might even remove the fuges at the end of the series for inspection and crow about how it’s all 3% stuff for peaceful civilian power stations. Many analysts speculate the Iranians use this method and that makes complete sense.
Managing hundreds of centrifuges whirling like racing engines full of radiactive gas in a series is not easy, it’s dangerous for the techs and engineers involved. The one big difference these days from the 1960s is the use of computers to monitor and optimize things like heat of friction, spin rate and signs of a wobble, radiation leakage, purity at all steps and so forth. Aha! If that network could be infected, it might send off a detailed stealthy streaming report on the day to day production results for us red-blooded ‘murikans to examine. If sensor data could be changed or read differently than it was supposed to be read, it could ruin entire production runs and maybe even cause expensive machinery to break down completely. At least that’s the gist of what I’m reading about it today. In an extreme situation it might even be possible for the infected network to produce material that was read as weapons grade, but is not weapons grade and therefore cannot achieve criticality — the a-bombs would fizzle not flash — but I haven’t seen any credible reports that this cyber attack was geared in that direction.
Opinions may differ, but in my view if the purported operation worked or even had a decent chance to work, and this isn’t just the usual spoofing or PR spin, more power to our men in radioactive black. That’s what we pay ’em to do and it beats the hell out of carpet bombing suspected facilities in just about every way imaginable — unless of course you are a draft dodging neocon advisor to Mitt Romney or a proud member of the 101st Keyboard Kommandos chomping at the bit for another trillion-dollar bloody boondoggle in the Middle East.


Well, because it wouldn’t help. Iran’s enemies are not going to wait to see whether those missiles actually explode before launching their counterattack. Turning Iran’s future nuclear arsenal into dummies won’t stop nuclear war – it’ll just delay one side getting destroyed for a few hours.
Unrelated: The ad I’m looking at on the right here is ‘Huffpo’s Pro-Iran bias – 33 Pro Iran Articles vs 8 Pro Iran Articles on ‘Shared Media’.’ What an odd ad. “Hate Iran? So do we! Come read OUR news!”
Don’t worry, it may still escalate into a boondoggle of some sort.
Not sure about Stuxnet, that one is old hat apparently…the Russkies have detected another one far more potent…
http://www.bbc.com/news/technology-18238326
Yeah, the news isn’t so much what Stuxnet is or what it did, the news is that it was confirmed that it was the US and Israel that made it. Apparently, this was seen as a good alternative to bombing the plant, which would escalate in a war. Did they really believe this would remain a secret and not lead to escalation too?
I’d definitely wanna be on the side getting hit with the fizzles, you know, if in the words of Gen Turdgenson I had to pick between ‘two admittedly bad but distinctly different scenarios …’
Well, yeah, but once missiles are launching, it’s not like the rest of the nuclear armed states are going to hold back.
Plus there’s the nukes we DON’T know about.
The US wants to prevent Iran from achieving nuclear electricity for the same reason it prevented Iran from purchasing oil refining equipment. If they have energy independence, they can control their own resources and start dictating terms to other countries.
As with Venezuela and elsewhere, the US “thinks” other countries don’t have the right to use their resources for their own benefit. “Our oil is under their sand” is still the mindset.
Stevarious (#6):
Or the nukes that no one will admit exist, like the 200 in Israel.
http://www.bendib.com/palestine/12-7-Vanunu.jpg
http://www.bendib.com/militarism/Weapons-of-Mass-destruction.jpg
This scenario depends on a herd of seriously incompetent quality assurance engineers and network designers … or pointy-haired bosses who don’t know what they’re doing. (Am I being redundant?)
I would not rely on production controls to tell me the isotopic composition of some production batch. I’d do individual assays of each production run’s products. This needs to happen at least to verify that the production process is making what it says it’s making.
I would not permit any computer network controlling production of nuclear weapons or devices to be connected to the Internet. Just no. No cables, no firewalls … just no. Every machine that lives on the inside “secure” network would be configured in a room in which there was no internet connection to the outside.
Firewalls? Clever-clever routers to the Internet? No. Just no. And once the system is up and running, it would take a really good reason to update the OS on the production systems. If it works, don’t fix it.
If I needed to get a new Linux distribution, I’d download its source and certify it by looking at a diff of the new version against the previous. Any backdoors in the source code (yeah, right) would be exposed. I’d carry the source in a freshly formatted thumb drive or CD-ROM to a different room, again with no internet connection, and there compile it. Depending on what I was building, there may or may not be a network connection from there to production. There would certainly be a staging lab where stuff gets tested before release.
Yes, it’s more expensive to do it that way, but the added cost is marginal compared to the cost of materials and value of the product … and the cost of having the product fail.
Network security is not rocket science. You just need to know what you’re doing and have people smarter than you examine your security design to find holes.
What dumb ass is building nuclear weapons components with computers connected to the Internet?
The shockingly large number of things in America and other 1st world countries that are completely unnecessarily connected to the internet boggles my mind sometimes.
Voting machines? Connected.
Nuclear power plants? Connected.
Trains. Flight controllers. Oil pipelines. Water filtration and distribution. All wired up.
The number of things unnecessarily connected to the internet is kind of scary.
I was thinking about that the other day, Stevarious, and it’s a great point. There are so many resources, open source apps and searchable data bases for example, now available on the Internet that many businesses these days have to be connected. The risks and rewards of that going forward might make a great post. Do you have any thoughts on that?
Just to clarify some things that you left ambiguous.
Enrichment is done on uranium, but not SFIAK on plutonium.
The fissile isotope of uranium U235 is 0.7% of naturally occuring uranium, almost all the rest being U238.
Some reactors (CANDU) can run on natural uranium, but most of the worlds reactors run on U enriched to a few % U235.
Bombs need somewhere around 90%+, though as you point out precise & accurate figures are hard to get.
Pu239 is the isotope wanted for fission. It is made by having U238 absorb neutrons. The difficulty from the POV of a bomb maker is that if some of the Pu239 in a plutonium production reactor absorb neutrons to become Pu240 which interferes with getting a big explosion. So for bomb making you take the uranium pellets out soon before much Pu240 has accumulated even though that limits the amount of Pu239 created.
My understanding is that the greater radioactivity of plutonium as well as differences in the chemistry of the volatile flouride compounds make isotope separation much harder for plutonium rather than uranium.
This webpage:
depletedcranium.com/why-you-cant-build-a-bomb-from-spent-fuel/
is a useful source, but appears to be currently umavailable.
The factory itself was not attached to the internet. The current scenario is that someone brought in an infected USB stick.
As for not being detected. It was only found out to exist once it did what should not have happened (that is infect a laptop) and escape into the wild.
As for removing the centrifuges before an inspection. Not likely since the IAEA is monitoring them more closely then fort Knox ever was. Aside from that the Iranians have never hidden their desire, and attempts, at getting 16% to 20% U235.
There is a legitimate use for that level of enrichment. Making medical isotopes. The problem being that the Iranians, from what I’ve read, do not have the capacity to turn that level of enriched U235 into working fuel rods.
Well, my point wasn’t that the businesses themselves have internet access, but that the actual systems that control these resources are connected to the internet. It’s completely unnecessary and dangerous to, say, have an oil pipeline monitoring and control system connected to the internet.
It’s downright insanity to have an air traffic control computer or a train routing control computer connected to the internet. Why strap a bomb to yourself and sneak onto a plane when you can take control of the air traffic controller’s computer and have him unintentionally direct two planes into the same flight path? Steer two trains into each other? Shut down a nuclear power plant?
These critical systems should all be off the grid. It’s insane that they are directly connected to such a massive security risk like the internet.
Internet connection has its ups and downs for various devices. The real issue is whether a device can be secure with any given connection to the outside; figure a solid firewall with only one port open and some kind of tunnel (IP-over-IP over something SSL-like, probably) to maintain direct service between two trusted nodes. If that can work, and it can be relied upon, then you’re golden. If it can’t, then you need to consider building a private network, if you’re networking it at all.
I will say that at least as far as transportation systems go, it’s reasonable (albeit perhaps politically impossible in some cases) to run all that information over a dedicated satellite or cellular link; there’s no need to ever connect the control systems on the train or plane to the passenger internet access anyway. But there’s already a huge investment in infrastructure in transportation systems to begin with; the real question is when this is practical for other systems. Power plants for example — you could hook it up to a dippy bird on your home computer, but you need onsite personnel in case one of the crossbeams goes out on the treadle, so you wouldn’t want to in the first place.
tl;dr Yeah, not everything should be connected to the internet, but it’s really a case-by-case deal.
IMHO if someone could gain control of the system to the end of making large numbers of people dead, it probably shouldn’t be on a publicly accessible network. There’s no such thing as 100% security.
+1 for obscure Simpson’s ref. :D
jimbaerg: So I have a question. I just had Chem and Nuke Engineering 515, and the professor said that while the enriched percentage was preferred to be high, that you could do more than enough mischief with 25% (the IAEA benchmark for nuclear power vs weaponization.) Where are you getting 90% from?