“Does anyone here know anything about ‘firewalls’?” asked Steve Walker, the CEO of Trusted Information Systems (TIS). If you read Mechanizing Proof [stderr] stw crops up a couple of times – he was one of the proponents of trustworthy design through formal verification, and TIS produced an evaluated version of UNIX known as Trusted Xenix.
I had come to TIS from Digital, following my mentor Fred Avolio, and had been working on the kernel build process for MACH – and I was languishing in a state of horror at how ugly it was. Life at Digital was better even though everyone knew the company was going out of business – I had written a firewall (the DEC SEAL) over my christmas break a few years earlier, and it turned into a pretty successful product that was bringing in about $2 million/year, until corporate product management took it away from me, re-branded it the AltaVista Firewall, and refused to answer customer requests if they asked for it under the old name. The ship was sinking and it was time to go.
I had considered two jobs, one to go to TIS with Fred and the other was to implement a firewall layer on a device called the ‘Lan Guardian’ that UUnet was building. I took a meeting with Rick Adams and talked over the progress and specs for the Lan Guardian, and guardedly told him it wouldn’t work. If I had gone to UUnet as “security guy” I’d have been at least a multimillionaire – they did a very successful IPO and got bought by Worldcom and the stock jumped through the roof. Oh, well. I wound up at TIS, hating MACH and surreptitiously playing DOOM. I was miserable.

The Clinton administration had just come in to power and was all ‘internet mad’ and apparently someone at White House Communications told someone “The White House will be on the internet” – so a phone call went from the White House to DARPA’s Brian Boesch, who was program manager for security, and a big supporter of stw and TIS, and there was a meeting with stw, Fred Avolio, and Steve Crocker and I got pulled into it and the next day it was decided we’d go down to DARPA and explain things to Boesch. Being an impulsive “can do” sort of guy, I decided to pull an all-nighter and write up a brief paper explaining what I thought the White House probably needed. It included:
- Firewall
- Secured email server (POP, at that time, did not have encyption; I proposed to hammer an encryption layer into a popular POP client and server implementation)
- Secure remote terminal (kermit and various modem based terminal emulators did not have encryption at that time; I proposed to build a kermit version with encryption and a server-side shim that handled the other side)
- FTP server; I proposed to build an FTP daemon that implemented a minimum service capability and had no file upload ability at all
When Boesch started asking “what should we do?” I pulled out my paper and handed it around. My bosses were respectively horrified, but that was how I had always behaved – I regularly got away with murder by claiming “I’m just really enthusiastic!” and pretending to be contrite. It turned out Brian Boesch was also the enthusiastic sort, so I suddenly found myself the project leader for a DARPA-funded research project for secure communications for the white house. I went home and started sketching out how the software was going to work, while DARPA arranged a T-1 line with internet access (through UUnet, at my suggestion) and a server for me to build things onto, and I registered “whitehouse.gov” and sent a request for a backbone route update to Rick Adams at UUnet, who promptly had a cow. A few days later I was in a meeting room at the Old Executive Office Building, in Washington, and I suggested “maybe I should register ‘whitehouse.com’ while I’m at it?” and ${nameless jackass} from the Executive office IT Department said “no, and if anyone does, we’ll just send them a ‘cease and desist.'” Obviously, I should have registered it and sold it later – the domain later fetched $2 million.
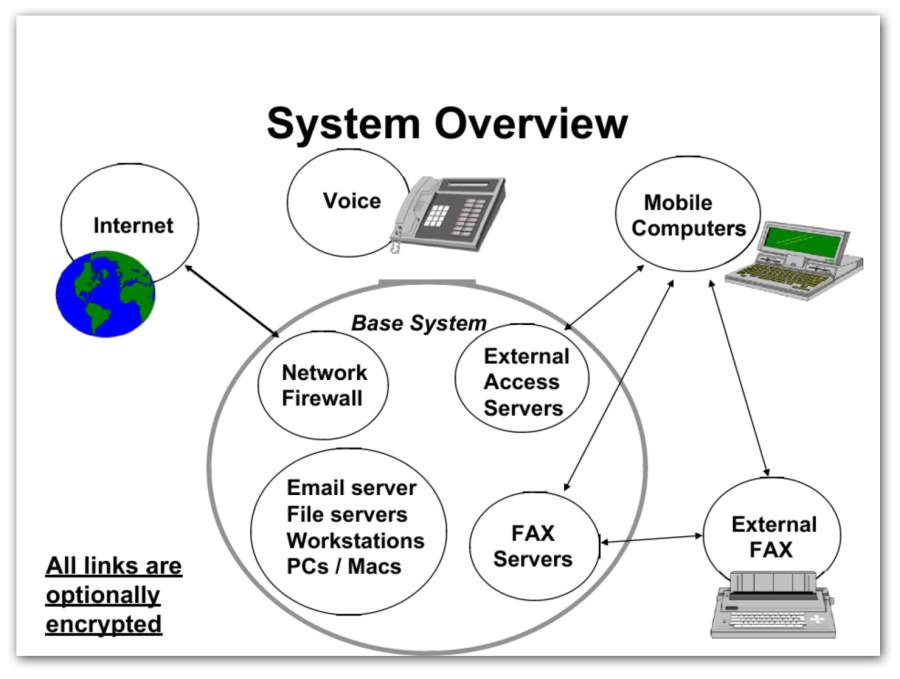
I never did get time to do the encrypted email/terminal, but I did the FTP server (it was part of the firewall toolkit add-ons) and the firewall stuff. The firewall was implemented as a set of cooperating components, which could be used in a variety of ways; I used them to build a highly secured server to receive email from the public, and to have an FTP area with government documents published by the White House. Meanwhile, the WWW was starting to happen, and some guys at NASA decided to make a web page for the White House. There were meetings, in which people demanded passwords so they could “add web pages to whitehouse.gov” and I had to explain that it was running a very stripped-down version of SunOS and there was actually no way to do what they wanted – which was true: there was not even a command shell on the system. If I needed to change anything, I had to drive in and do it from the console via a magnetic tape. That security architecture seemed good to me: it forced all administration to be console, which meant physical access, which was good security because the whitehouse.gov system was actually sitting next to my desk up at TIS in Glenwood, MD and not in Washington, at all.
There were a lot of funny catastrophes related to the project, and I don’t think I should go into them at length, but it was a fun and busy time for me. I realized pretty quickly that Washington was full of bureaucrats whose job was to not accomplish anything, while fighting each other tooth and nail to control who was most important. That annoyed me immensely. I also came to have a lot of respect (and some fear) for the US Secret Service – they were top-notch and very professional, but they were still cops and still stupid. But they were really serious and dangerous. There were a few sessions at Department of Treasury where I taught classes in how to back-track email, and validate network transactions, attended by Secret Service strike teams that looked like ninjas and who carried H&K MP5pdws – nothing but the best (and most expensive!) gear for them.
One night, my phone rang at 3:00am, just after I had gone to bed, “can you get down here?” I hopped in the car and drove like a bat out of hell from Baltimore. I got through security and into the briefing room and was told: “our security experts have discovered that there is a ‘service’ running on “whitehouse.gov” on port 19 – the system has been hacked and you need to look at it.” 19? That’s chargen. I actually had put a thingie in place that looked like the chargen server but fired off an alarm if it got connections, because the edge-router was supposed to be blocking those ports. It was an early example of one of my ‘burglar alarms’ and it had fired and there were emails waiting in my in-box; I just hadn’t woken up and read them yet because I was too busy driving to Washington. Oh, a detail I forgot: this occurred after “whitehouse.gov” finally moved down to Washington, so it was on a network that I no longer controlled. And there was the WWW server that NASA had built, sitting there, too. So it was possible for someone (with authorization) to plug in a laptop on that network, and port-scan “whitehouse.gov” from within the security perimeter – something I specifically expected to never happen, hence the alarm. It took many cups of coffee and a lot of whiteboard-scribbling to calm everyone down. Then I said, “Alright. Now that you’re all calmed down, can I scream at you for allowing something like that, without understanding what you’re doing?” Because, see, I knew who the tame hacker was by that point, and he was nobody that anybody should let on anyone’s network – even if there were goons with guns in the room.
A few years later, I decided to put something on my resume about my doing the “whitehouse.gov” email server, and ${nameless jackass} came up to me at a conference and said “you’re not allowed to mention that you did work here, update your resume.” It was a great pleasure to tell him to pound sand and that, since I was self-employed, I suppose he could call my mother and complain to her. Then I said “mom’s used to getting calls like that, so you won’t get very far.”
When I set the system up, I wrote a couple pieces of code that ingested email and compacted out multiple copies. That was because Rush Limbaugh’s mailing list software sucked and there were at least 300 people who thought it was funny to subscribe [email protected] to Rush’s email announcement list. The server would ingest those and +1 to a message count and that was it. It was a handy form of compression. Then, I would walk to the console once a week and make a set of floppy discs with the archive, and fedex them down to Washington. I always wondered what happened to the floppies – technically they are ‘presidential records’ and subject to FOIA. They represent the earliest known examples of my attempting to write legibly.
The whole “firewalls” thing was painful for stw and TIS, because it was seen as an untrustworthy commercial security product. There was debate as to whether or not the company should get into that business. A great deal of effort was expended to attack and defend the idea of commercial security products and – in the end – money won. TIS went public and suddenly everyone was rich, especially the old-timers who had worked there for years. Then Network Associates (MacAfee) bought TIS and the stock screamed through the ceiling and everyone was very, very rich. I did OK, too, but there was a divorce settlement and that’s where the money went. But I got to watch and participate in (if not shape) a new industry, and that was pretty exciting and exhausting and fun.

After the Reagan Administration, presidential records were a big deal (the stuff about the Reagan team’s email backups being accidentally wiped was complete bullshit) and everyone on the Clinton team including Hillary got briefings on presidential records from White House Counsel. I got a second-hand version of the briefing because I was handling presidential records – technically I was creating them; I remember being told not to write anything down.
The floppy disk thing was an important part of the security architecture. I figured that it was going to be mighty hard to hack across a one-way floppy-packet interface.
I had left TIS and struck out as a consultant by the time that things got fully ugly and there was a WWW server down in the computer room in Washington. I would have never allowed that to happen. A few years later a hacker I know started ribbing me at a conference, about the architecture of that network, and I realized that he thought I was responsible for it – and that he had been inside of it. Ever since then I was careful to always mention that the system was in good condition when I turned it over to White House IT staff, but that the nameless bureaucrats had almost certainly messed it up. Not my problem.
I still have all of those old documents and source code (and emails!) but unfortunately I can’t seem to decode some of the old MS-Office docs. I am still trying to locate my Message From The Swedish Prime Minister. We’ll see what I can dig up (as long as it’s minimal effort)
Powerpoint has, literally, framed my life. I’m not sure what I think of that, so I’ll just leave it there. When Powerpoint 1.0 came out, they gave copies to all the sales support people at Digital (to run on our new butt-ugly beige Digital laptops) and I decided it was as useful tool, and invested the time to thoroughly master it.

Wow – what an incredible thing to have been a part of. That is really interesting. I love that you could tell ${nameless jackass} to take a flying leap… and why would you not be able to say what you did? His request was ridiculous.
Thanks for the inside account.
kestrel@#1:
I love that you could tell ${nameless jackass} to take a flying leap… and why would you not be able to say what you did? His request was ridiculous.
There is a great deal of “White House Fairy Dust” spread about – I was amazed by the number of people who would jump through a few hoops just to say “I worked at the White House.” Usually they figured out that the whole thing was a dysfunctional mess, completed their project, and got out of there.
Inside the Washington Bubble the desires of the White House are all-important. I’ll tell another story about that (actually, it’s already queued) in a couple days. They expect to be able to control what you do, or what you say, because there’s the threat that they won’t invite you back. Access is basically all they’ve got to trade on so when I started mentioning that I’d done that project, ${nameless jackass}’ currency was not being respected. I never agreed to a non-disclosure and I never touched anything classified, so they the only hold they had over me was access – and I had no interest in going back there anyhow.
It was a bit of a shock to realize that The White House is a scam. They don’t have the power or money to accomplish anything themselves – for example, they couldn’t buy a T-1 line and a computer, they had to get DARPA to pay for it. For example, at one point, the White House IT staff had a meeting about connecting a certain computer to the network – there was a question about getting a network adapter – that was what the whole meeting was about: who was going to pay for the network adapter. I had a huge collection of hardware components at home from when I worked at Digital, and I just brought in an adapter the next day. Then there was a meeting about who was going to pay for its installation. Seriously. This was back in the day when my brief case was always full of cable, screwdrivers, a mini soldering gun – the Secret Service security at the door loved my brief case, especially since I carried an X-ray proof Halliburton Zero and it had to be hand-inspected. Anyhow, I just installed the damn network adapter. There were meetings about everything. I am sure I was horribly badly-behaved; I was not the patient, un-opinionated, respectful, mild-mannered “team player” I am now.
@Marcus, #3: They had meetings about how to pay for stuff?! That is so weird. Well… OK, maybe I can understand a little, but I don’t know anything about White House finances etc. I do know it’s all public funds and there at least *should be* great scrutiny on how those funds are spent: I don’t know if they do, but they *should* have to go through an audit every year. Those types of big audits are difficult to get through with no findings at all. It would be enough to make anyone jumpy about money they spent, how they did it and whether they could back it up and justify the expense.
“I was not the patient, un-opinionated, respectful, mild-mannered “team player” I am now.” I nearly choked to death on my water. I really should know better than to drink anything while reading your blog.